F5 101 - Application Delivery Fundamentals
Which two destination pods should be used in a default active FTP Session? (Choose two)
An administrator needs to do the following
* install a load balancer in front of an existing application
* test application performance
* avoid reconfiguration of the application server
* avoid interruption of users accessing the application
A BIG IP Administrator wants to add a new VLAN (VLAN 40) to an LACP trunk (named LACP01) connected to the BIG-IP device Mufti VLANS exist on LACPO1.Which TMSH command should the BIGIP Administrator issue to add the new VLAN to the existing LACP trunk?
ATP administrator recently added a new VLAN and needs to confirm that the BIG IP sees traffic on this VLAN. The VLAN is untagged on interface 1.1 and is named VLAN704 in the BIG IP Configuration Unity.
Which tool should be used to generate a packet capture that shows all traffic on this VLAN?
The BIG-IP device has the following configured routes:
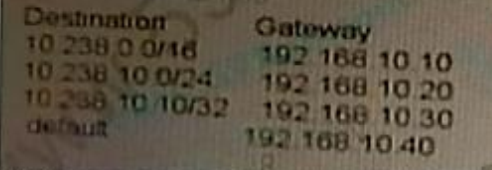
Which gateway will be chosen to send the packet to the destination 10 238 10 11?
HTTPS traffic is being passed from behind a NAT router, through a load balancer, to servers without being decrypted.
What is the F5-recommended persistence method in this situation?
in which scenario would an SSL VPN solution have an advantage over an IPSec VPN?
An administrator security policy defines allowed URLs, file types and parameter values Which security model is the administrator using?
An administrator is updating private keys used for SSL encryption from 1024 to 2048 bits. Which possible effect should the administrator consider when performing this activity?
AD VLAN must be created with an 802.19 tag of 705 on interface 11. What is the proper TSH command to create this new VLAN on the BIG-IP?



