Checkpoint 156-315.81 - Check Point Certified Security Expert R81.20 ( 156-315.81.20 )
You have a Geo-Protection policy blocking Australia and a number of other countries. Your network now requires a Check Point Firewall to be installed in Sydney, Australia.
What must you do to get SIC to work?
In which formats can Threat Emulation forensics reports be viewed in?
Which is NOT a SmartEvent component?
Which tool is used to enable ClusterXL?
What command lists all interfaces using Multi-Queue?
Fill in the blank: The R81 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows then as prioritized security events.
You need to change the number of firewall Instances used by CoreXL. How can you achieve this goal?
What will SmartEvent automatically define as events?
What is the recommended number of physical network interfaces in a Mobile Access cluster deployment?
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
Which NAT rules are prioritized first?
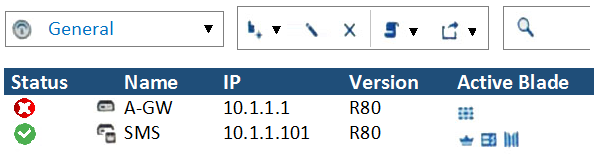
What does it mean if Deyra sees the gateway status? (Choose the BEST answer.)
Which Check Point feature enables application scanning and the detection?
Office mode means that:
You can access the ThreatCloud Repository from:



