Checkpoint 156-315.81 - Check Point Certified Security Expert R81.20 ( 156-315.81.20 )
Fill in the blank: The R81 utility fw monitor is used to troubleshoot ______________________.
What are the different command sources that allow you to communicate with the API server?
What SmartEvent component creates events?
What is true about VRRP implementations?
Which command would disable a Cluster Member permanently?
In R81, how do you manage your Mobile Access Policy?
R81.20 management server can manage gateways with which versions installed?
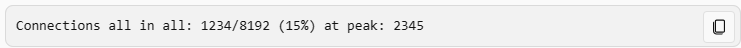
Which command can you use to verify the number of active concurrent connections?
CoreXL is supported when one of the following features is enabled:
Check Point recommends configuring Disk Space Management parameters to delete old log entries when available disk space is less than or equal to?
Your manager asked you to check the status of SecureXL, and its enabled templates and features. What command will you use to provide such information to manager?
Advanced Security Checkups can be easily conducted within:
SSL Network Extender (SNX) is a thin SSL VPN on-demand client that is installed on the remote user’s machine via the web browser. What are the two modes of SNX?
The fwd process on the Security Gateway sends logs to the fwd process on the Management Server via which 2 processes?
Which of the following is a new R81 Gateway feature that had not been available in R77.X and older?