CIW 1D0-541 - CIW v5 Database Design Specialist
Which of the following definitions best describes an entity?
Which database security technique prevents invalid data from being entered into the database?
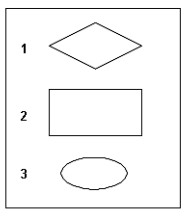
Consider the symbols shown in the exhibit. Which of the following correctly identifies these symbols when used in an entity-relationship (ER) diagram?
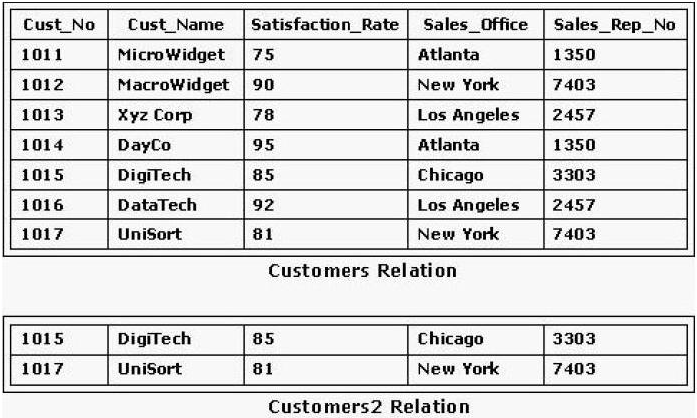
Consider the following relations shown in the exhibit. Which of the following SQL statements would return the Customers2 relation from the Customers relation?
Your enterprise must decide whether to use a database management system. Which of the following best describes the functionality of a DBMS?
Which type of relational integrity is violated if a primary key in a database has a null value?
Consider the following relation definition:
STUDENT(
Student_Number: integer NOT NULL
Name: variable length character string length 20 NOT NULL)
Primary Key Student_Number
HOUSING(
Housing_ID: integer NOT NULL
Student_Number: integer NOT NULL
Building: variable length character string length 25 NOT NULL)
Primary Key Housing_ID
Foreign Key Student_Number References
STUDENT(Student_Number)
ON DELETE NO CHECK
ON UPDATE
Which integrity constraint is violated in this relation definition?
A theta-join can be viewed as:
Which of the following definitions applies to all types of databases?
Which mechanism provides database users with controlled access to the database through the use of virtual tables?



