CIW 1D0-610 - CIW Web Foundations Associate
Consider the network configuration shown in the command prompt:
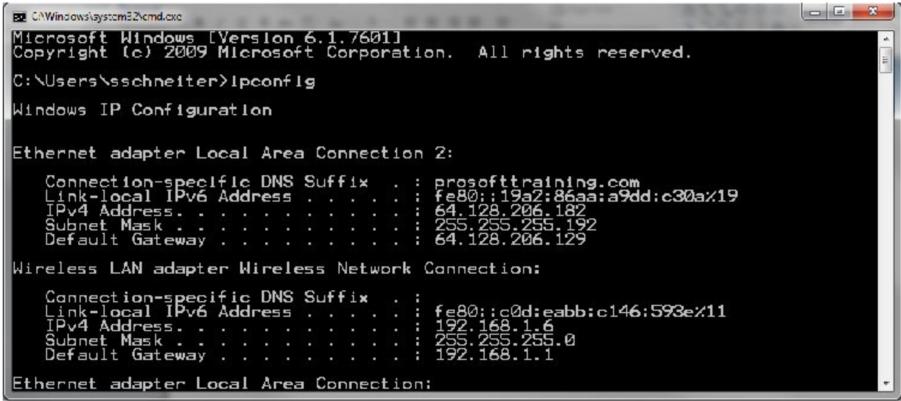
What does the Default Gateway identify?
Ron has an older computer to which he frequently downloads and saves company files. He recently noticed that he was running low on disk space and decided to delete many old files that he no longer needed. He now notices that it takes a long time to open or save documents to his hard drive. Which maintenance task can help?
Web developers typically include comments in their code for which reason?
The Internet has enabled many new anti-social activities, such as online stalking, cyber bullying, and addiction to solitary online activities. Which choice is the most feasible way for schools and parents to reduce cyber bullying?
You want to enable wireless security on your Android device and your Linux system. Which of the following is a disadvantage of Wired Equivalent Privacy (WEP)?
When a developer wants to center a paragraph of text, which code should she use?
When previewing a Web page using a GUI HTML editor, you will:
You have recently purchased a new wireless router. You would like to configure a name for your wireless network so that you can easily identify it when scanning available wireless networks. Which term describes this wireless network device name?
Carlos is the Information Technology (iT) administrator for a small company. Over the past year, employees have been using their personal mobile devices and smart phones for business use. This has reduced costs of purchasing new devices for employees. Carlos is now considering whether he should stop supplying employees with company phones and instead require all employees to use their personal smart phones for work. How can Carlos address the most significant security vu inerrability?
You are configuring an e-mail client to connect to your e-mail account. Which of following is required to set up the e-mail account?



