Cisco 200-901 - DevNet Associate (DEVASC)
Which two statements about JSON and XML are true? (Choose two.)
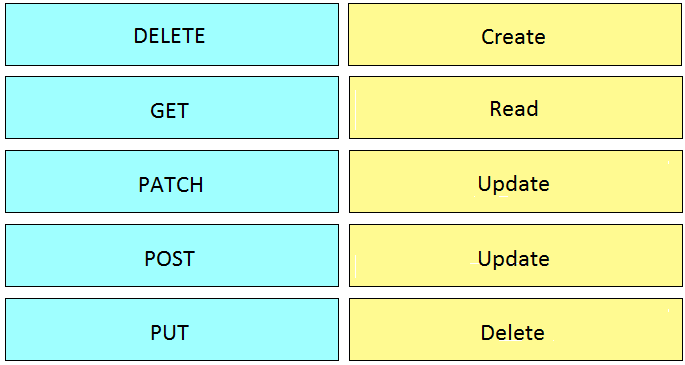
: 19 DRAG DROP
Drag and drop the HTTP methods from the left onto their generally accepted corresponding create, read, update, and delete operations on the right.
Which API is used to obtain data voicemail ports?
What are the two principles of an infrastructure as code environment? (Choose two)
Which principle is a value from the manifesto for Agile software development?
what is an advantage of a version control system?
What are two security benefits of a Docker-based application?
Which two use cases are supported by Meraki APIs? (Choose two.)
The project is migrated to a new codebase, the “old_project†directory must be deleted. The directory has multiple read-only files, and it must be deleted recursively without prompting for confirmation. Which bash command must be used?
Which action resolves a 401 error in response to an HTTP GET that is issued to retrieve statement using RESTCONF on a CSR 1000V?