F5 201 - TMOS Administration
During a high-demand traffic event, the BIG-IP Administrator needs to limit the number of new
connections per second allowed to a Virtual Server.
What should the administrator apply to accomplish this task?
A BIG-IP Administrator is checking the BIG-IP device for known vulnerabilities. What should the 8IG-IP Administrator upload to BIG-IP iHealth for further analysis?
Refer to the exhibit.
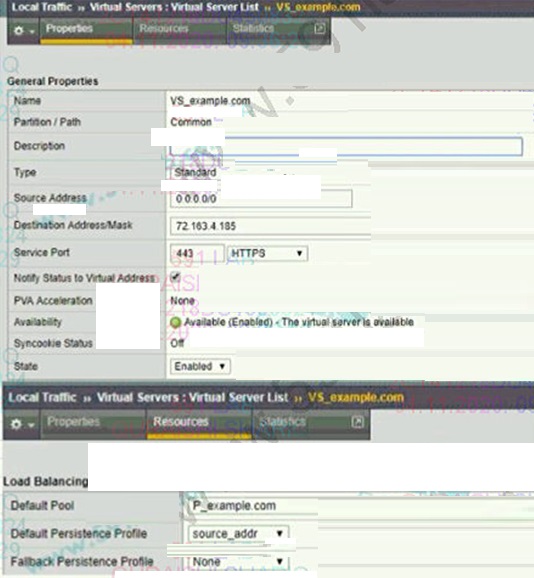
An organization is reporting slow performance accessing their Intranet website, hosted in a public cloud. All employees use a single Proxy Server with the public IP of 104.219.110.168 to connect to the Internet. What should the BIG-IP Administrator of the Intranet website do to fix this issue?
Active connections to pool members are unevenly distributed. The load balancing method is Least Connections (member) Priority Group Activation is disabled. What is a potential cause of the event distribution?
A BIG-IP Administrator remotely connects to the appliance via out-of-band management using https://mybigip mycompany net. The management portal has been working all week. When the administrator attempts to login today, the connection times out. Which two aspects should the administrator verify? (Choose two)
Administrative user accounts have been defined on the remote LDAP server and are unable to log in to
the BIG-IP device.
Which log file should the BIG-IP Administrator check to find the related messages?
A web server administrator informs the BIG-IP Administrator that web servers are overloaded Starting next month, the BIG-IP device will terminate SSL to reduce web server load. The BIG-IP device is ready using client SSL client profile and Rules on HTTP level. What actions should the BIG-IP Administrators to achieve the desired configuration?
Refer to the exhibit.
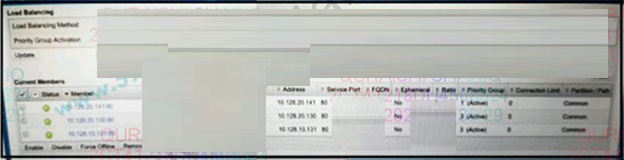
How are new connections load balanced?
Which method is recommended for creating a new user from the CLI?
A BIG-IP Administrator needs to view the CPU utilization of a particular Virtual Server. Which section of the Configuration Utility should the administrator use for this purpose?



