VMware 2V0-41.24 - VMware NSX 4.X Professional V2
When a stateful service is enabled for the first time on a Tier-0 Gateway, what happens on the NSX Edge node?
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
What are four NSX built-in role-based access control (RBAC) roles? (Choose four.)
Where does an administrator configure the VLANs used in VRF Lite? (Choose two.)
Which steps are required to activate Malware Prevention on the NSX Application Platform?
Which choice is a valid insertion point for North-South network introspection?
In which VPN type are the Virtual Tunnel interfaces (VTI) used?
When collecting support bundles through NSX Manager, which files should be excluded for potentially containing sensitive information?
A customer has a network where BGP has been enabled and the BGP neighbor is configured on the Tier-0 Gateway. An NSX administrator used the get gateways command to retrieve this information:
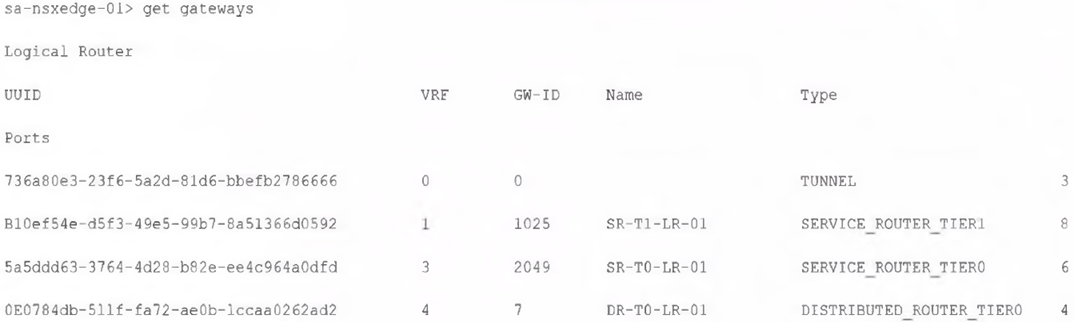
Which two commands must be executed to check BGP neighbor status? (Choose two.)
Which CLI command is used for packet capture on the ESXi Node?



