Cisco 300-410 - Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI)
Refer to the exhibit.
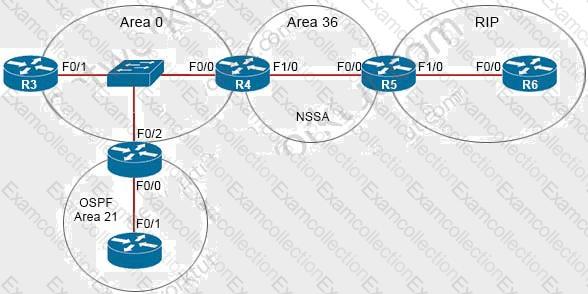
The network engineer configured the summarization of the RIP routes into the OSPF domain on R5 but
still sees four different 172.16.0.0/24 networks on R4. Which action resolves the issue?
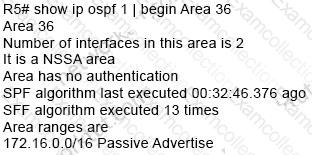
Refer to the exhibit. R1 lost its directly connected EIGRP peer 172.16.33.2 (SW1). Which configuration resolves the issue?
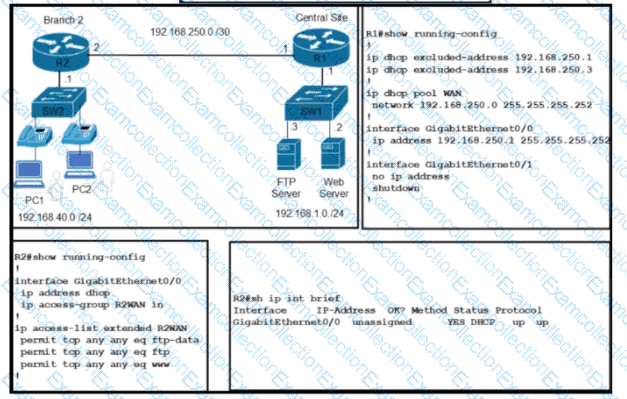
Refer to the exhibit. Which configuration is required for R2 to get the IP address from the DHCP server?
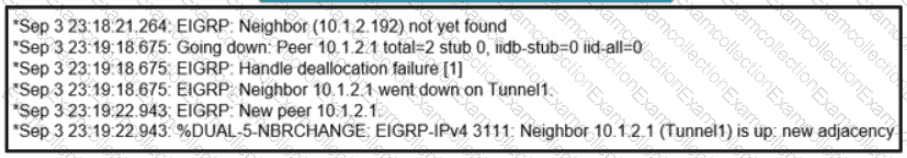
Refer to the exhibit. Which configuration command establishes an EIGRP neighbor adjacency between the hub and spoke?
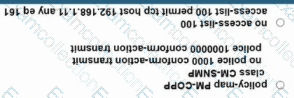
The network administrator configured CoPP so that all SNMP traffic from Cisco Prime located at 192.168.1.11 toward the router CPU is limited to 1000 kbps. Any traffic that exceeds this limit must be dropped.
access-list 100 permit udp any any eq 161
class-map CM-SNMP
match access-group 100
policy-map PM-COPP
class CM-SNMP
police 1000 conform-action transmit
!
control-plane
service-policy input PM-COPP
The network administrator is not getting the desired result for the SNMP traffic and SNMP traffic is getting dropped frequently. Which set of configurations resolves the issue?

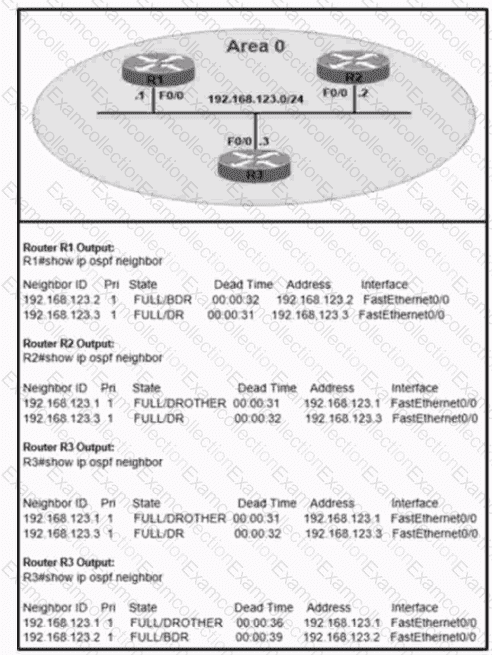
Refer to the exhibit. An administrator wanted to make R1 always elected as DR. R2 as BDR. and R3 as DROTHER but could not achieve the desired results. Which two configurations resolve the issue? (Choose two.)
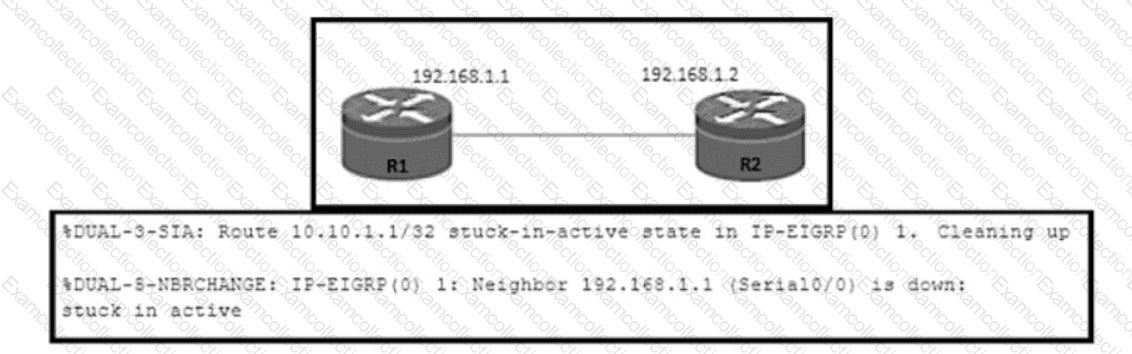
Refer to the exhibit. An engineer notices a connectivity problem between routers R1 and R2. The frequency of this problem is high during peak business hours. Which action resolves the issue?
:593
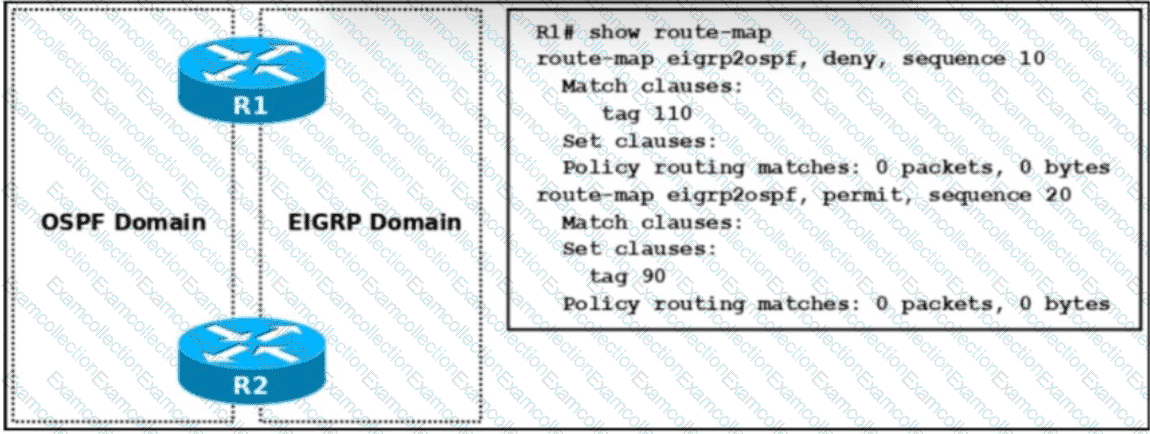
Refer to the exhibit. Which two configurations are required on R2 to prevent a routing loop caused by the redistribution from OSPF back into EIGRP? (Choose two.)
Refer to the exhibit.
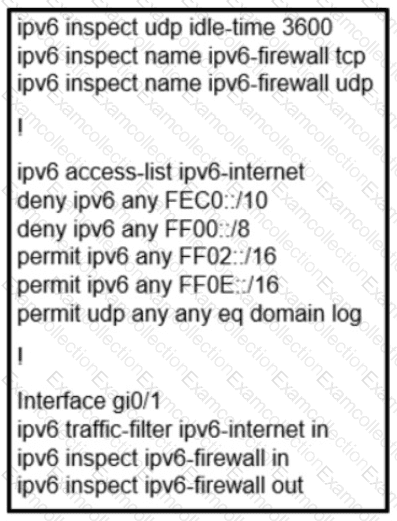
A network administrator configured name resolution for IPv6 traffic to be allowed through an inbound access list. After the access list is applied to resolve the issue, name resolution still did not work. Which action does the network administrator take to resolve the name resolution problem?
Refer to the exhibit.
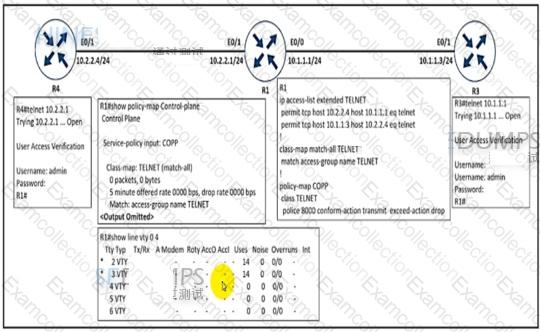
An engineer implemented CoPP to limit Telnet traffic to protect the router CPU. It was noticed that the Telnet traffic did not pass through CoPP Which configuration resolves the issue?
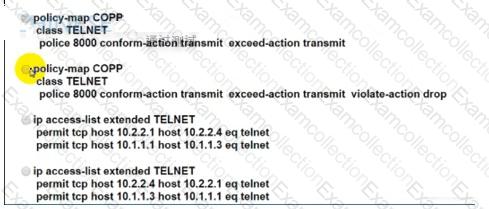
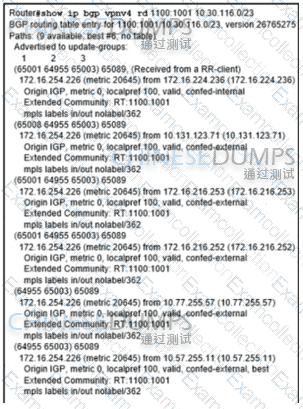

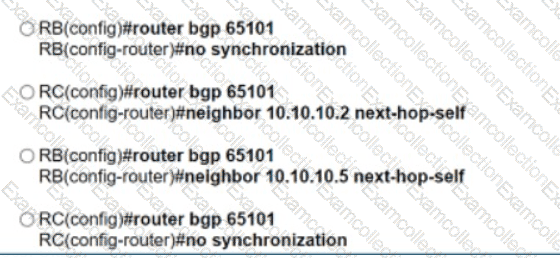
Refer to the exhibit. An engineer configured BGP and wants to select the path from 10.77.255.57 as the best path instead of current best path. Which action resolves the issue?
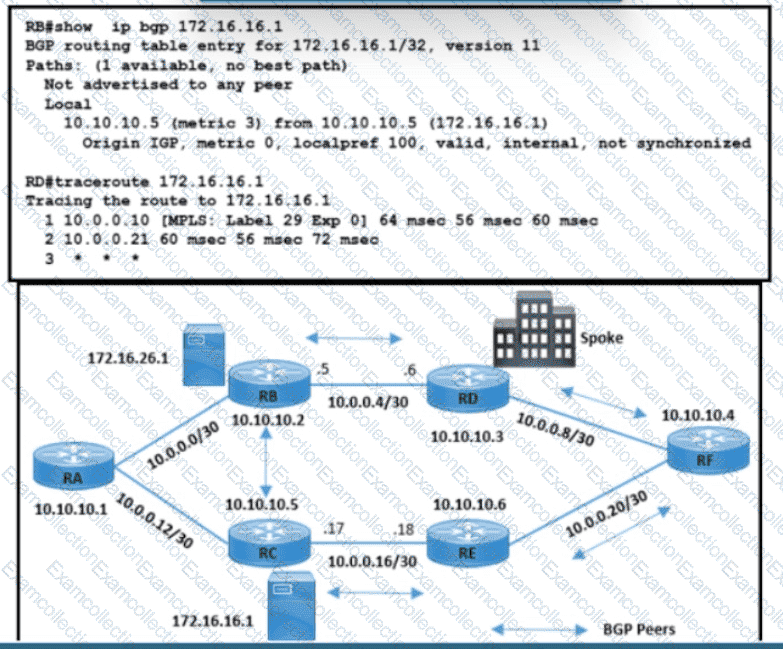
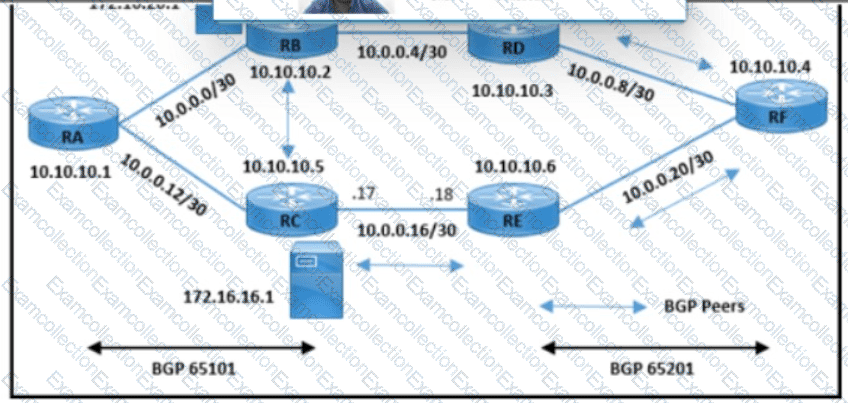
Refer to the exhibit A customer reported an issue with a fiber link failure between RC and RE Users connected through the spoke location face disconnection and packet drops with the primary email server (172.16.16.1) but have no issues with the backup email server (172.16.26.1). All the router loopback IPs are advertised through the OSPF protocol. Which configuration resolves the issue?
Which feature is required for IPv6 Source Guard to block traffic arriving on the server interface from unknown sources?
What are the two reasons for RD and VPNv4 addresses in an MPLS Layer 3 VPN? (Choose two.)
Refer to the exhibit.
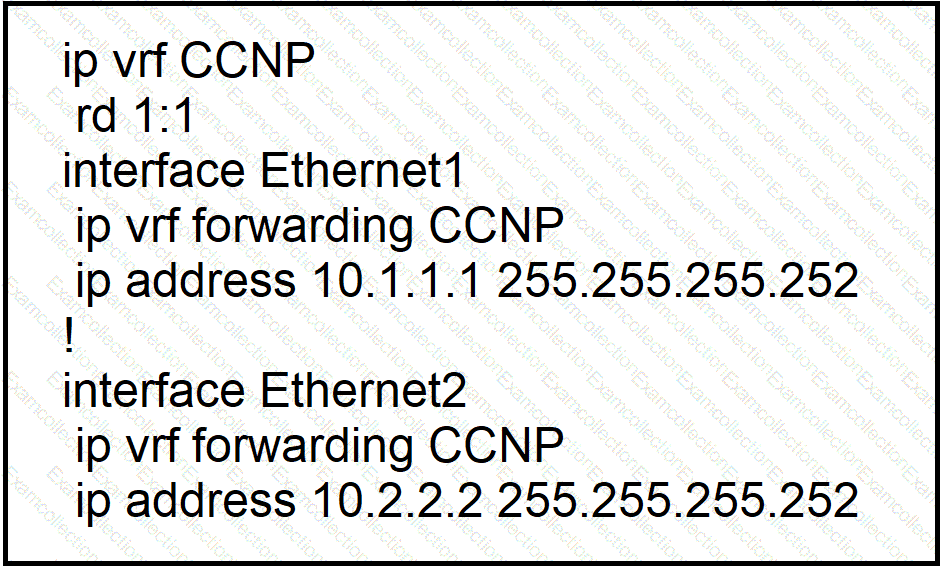
Which configuration enables OSPF for area 0 interfaces to adjacency with a neighboring router with the same VRF?



