Cisco 300-415 - Implementing Cisco SD-WAN Solutions (300-415 ENSDWI)
A policy is created to influence routing in the network using a group of prefixes. What policy application will achieve this goal when applied to a site list?
Which cloud based component in cisco SD-WAN is responsible for establishing a secure connection to each WAN edge router and distributes routers and policy information via omp?
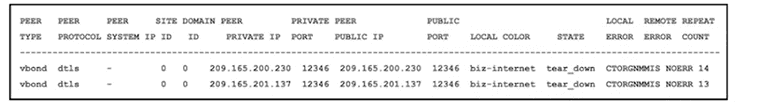
Refer to the exhibit An engineer is getting a CTORGNMMIS error on a controller connection Which action resolves this issue?
An engineer must avoid routing loops on the SD-WAN fabric for routes advertised between data center sites Which BGP loop prevention attribute must be configured on the routers to meet this requirement?
Which two actions are necessary to set the Controller Certificate Authorization mode to indicate a root certificate? (Choose two)
Which two types of SGT propagation are supported by Cisco TrustSec? (Choose two.)
For data plane resiliency, what does the Cisco SD-WAN software implement?
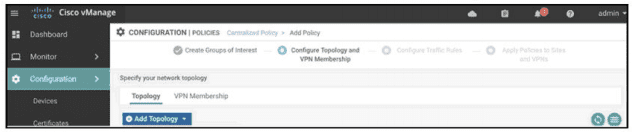
Refer to the exhibit. An administrator is configuring a policy in addition to an existing hub-and-spoke policy for two sites that should directly communicate with each other. How is this policy configured?
Which two virtualized environments are available for a company to install the controllers using the on-premises model? (Choose two )
An organization requires the use of integrated preventative engines, exploit protection, and the most updated and advanced signature-based antivirus with sandboxing and threat intelligence to stop malicious attachments before they reach users and get executed. Which Cisco SD-WAN solution meets the requirements?



