Cisco 300-710 - Securing Networks with Cisco Firepower (300-710 SNCF)
Which report template field format is available in Cisco FMC?
An engineer must implement Cisco Secure Firewall transparent mode due to a new server recently being added that must communicate with an existing server that is currently separated by the firewall. Which implementation action must be taken next by the engineer to accomplish the goal?
How should a high-availability pair of Cisco Secure Firewall Threat Defense Virtual appliances be deployed to Cisco Secure Firewall Management Center?
Which command-line mode is supported from the Cisco Firepower Management Center CLI?
An engineer must perform a packet capture on a Cisco Secure Firewall Threat Defense device to confirm the MAC address of the host using IP address 192.168.100.100 while troubleshooting an ARP issue. What is the correct tcpdump command syntax to ensure that the MAC address appears in the packet capture output?
What is a feature of Cisco AMP private cloud?
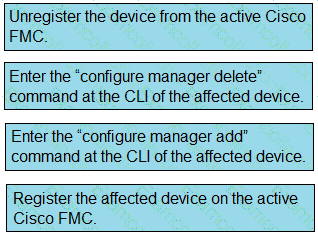
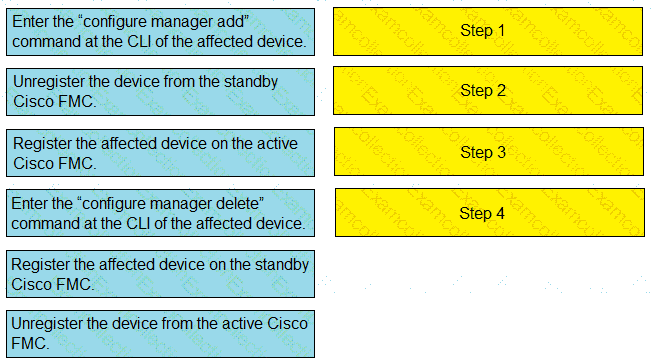
Drag and drop the steps to restore an automatic device registration failure on the standby Cisco FMC from the left into the correct order on the right. Not all options are used.
An administrator is attempting to add a new FTD device to their FMC behind a NAT device with a NAT ID of NAT001 and a password of Cisco0420l06525. The private IP address of the FMC server is 192.168.45.45. which is being translated to the public IP address of 209.165.200.225/27. Which command set must be used in order to accomplish this task?
An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco FTD devices. Which action must be taken to ensure that each context on the Cisco ASA is logically separated in the Cisco FTD devices?
An engineer is configuring a Cisco Secure Firewall Threat Defence device managed by Cisco Secure Firewall Management Centre. The device must have SSH enabled and the accessible from the inside interface for remote administration. Which type of policy must the engineer configure to accomplish this?