Cisco 300-715 - Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE)
Which two external identity stores support EAP-TLS and PEAP-TLS? (Choose two.)
An administrator must provide wired network access to unidentified Cisco devices that fail 802.1X authentication. Cisco ISE profiling services must be configured to gather Cisco Discovery Protocol and LLDP endpoint information from a Cisco switch. These configurations were performed:
• configured switches to accept SNMP queries from Cisco ISE
• enabled Cisco Discovery Protocol and LLDP on the switches
• added the switch as a NAD to Cisco ISE
What must be enabled to complete the configuration?
An administrator is configuring the Native Supplicant Profile to be used with the Cisco ISE posture agents and needs to test the connection using wired devices to determine which profile settings are available. Which two configuration settings should be used to accomplish this task? (Choose two.)
What is an advantage of using EAP-TLS over EAP-MS-CHAPv2 for client authentication?
An engineer is tasked with placing a guest access anchor controller in the DMZ. Which two ports or port sets must be opened up on the firewall to accomplish this task? (Choose two.)
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from the Cisco ISE node?
Refer to the exhibit.

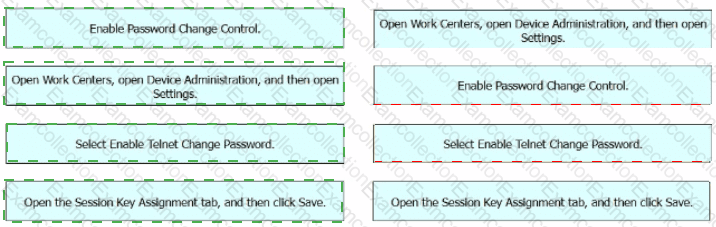
An engineer must configure Cisco ISE to be used as the TACACS+ server for any administrator that signs into the router. Users must be able to change their Telnet password through the TACACS+ server. Drag and drop the configuration steps from the left into the sequence on the right.

A network administrator is configuring client provisioning resource policies for client machines and must ensure that an agent pop-up is presented to the client when attempting to connect to the network Which configuration item needs to be added to allow for this'?
Which two endpoint compliance statuses are possible? (Choose two.)
Which type of identity store allows for creating single-use access credentials in Cisco ISE?