Cisco 300-730 - Implementing Secure Solutions with Virtual Private Networks (SVPN)
Refer to the exhibit.
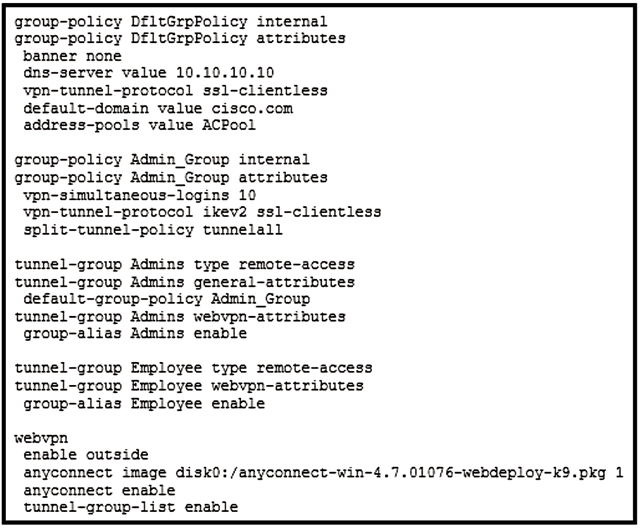
Which VPN technology is allowed for users connecting to the Employee tunnel group?
Which technology is used to send multicast traffic over a site-to-site VPN?
What uses an Elliptic Curve key exchange algorithm?
Which benefit of FlexVPN is a limitation of DMVPN using IKEv1?
Cisco AnyConnect clients need to transfer large files over the VPN sessions. Which protocol provides the best throughput?
Which parameter is initially used to elect the primary key server from a group of key servers?
Refer to the exhibit.
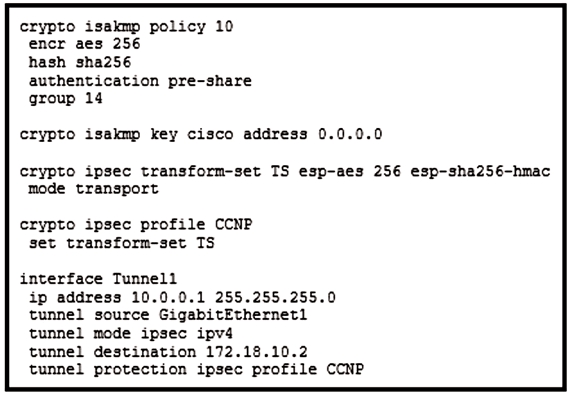
Which VPN technology is used in the exhibit?
Which redundancy protocol must be implemented for IPsec stateless failover to work?
What are two functions of ECDH and ECDSA? (Choose two.)
Refer to the exhibit.
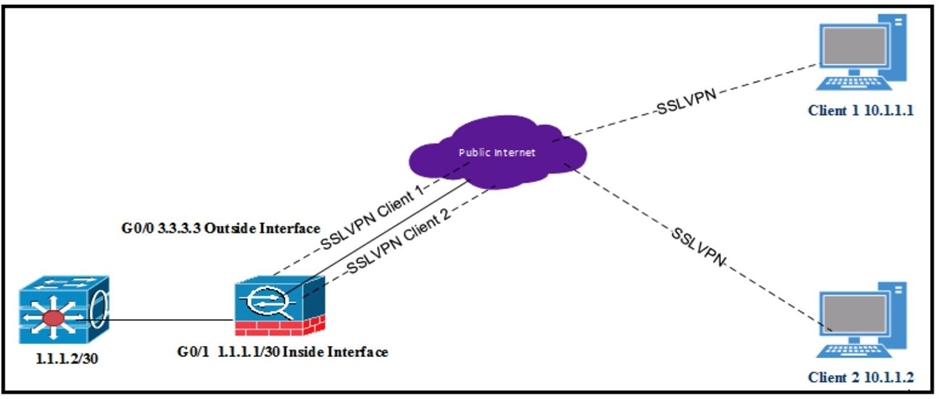
All internal clients behind the ASA are port address translated to the public outside interface that has an IP address of 3.3.3.3. Client 1 and client 2 have established successful SSL VPN connections to the ASA. What must be implemented so that "3.3.3.3" is returned from a browser search on the IP address?



