ECCouncil 312-49 - Computer Hacking Forensic Investigator
Gill is a computer forensics investigator who has been called upon to examine a seized computer. This computer, according to the police, was used by a hacker who gained access to numerous banking institutions to steal customer information. After preliminary investigations, Gill finds in the computer’s log files that the hacker was able to gain access to these banks through the use of Trojan horses. The hacker then used these Trojan horses to obtain remote access to the companies’ domain controllers. From this point, Gill found that the hacker pulled off the SAM files from the domain controllers to then attempt and crack network passwords. What is the most likely password cracking technique used by this hacker to break the user passwords from the SAM files?
In what way do the procedures for dealing with evidence in a criminal case differ from the procedures for dealing with evidence in a civil case?
Pagefile.sys is a virtual memory file used to expand the physical memory of a computer. Select the registry path for the page file:
When performing a forensics analysis, what device is used to prevent the system from recording data on an evidence disk?
You are called in to assist the police in an investigation involving a suspected drug dealer. The suspects house was searched by the police after a warrant was obtained and they located a floppy disk in the suspects bedroom. The disk contains several files, but they appear to be password protected. What are two common methods used by password cracking software that you can use to obtain the password?
What does mactime, an essential part of the coroner's toolkit do?
What do you call the process in which an attacker uses magnetic field over the digital media device to delete any previously stored data?
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
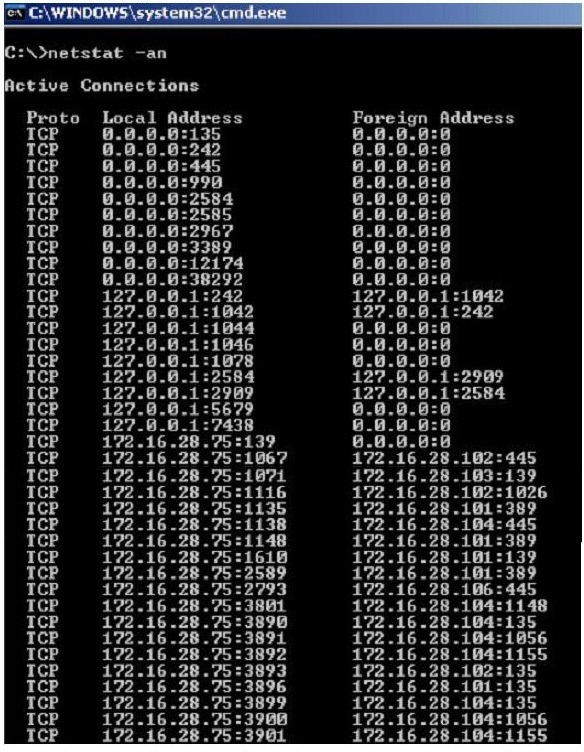
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
Â
Which of the following data structures stores attributes of a process, as well as pointers to other attributes and data structures?
Which of the following options will help users to enable or disable the last access time on a system running Windows 10 OS?
What technique is used by JPEGs for compression?
Email archiving is a systematic approach to save and protect the data contained in emails so that it can be accessed fast at a later date. There are two main archive types, namely Local Archive and Server Storage Archive. Which of the following statements is correct while dealing with local archives?
Which response organization tracks hoaxes as well as viruses?
Which of the following commands shows you the username and IP address used to access the system via a remote login session and the type of client from which they are accessing the system?
Which of the following processes is part of the dynamic malware analysis?



