ECCouncil 312-49 - Computer Hacking Forensic Investigator
Adam, a forensic analyst, is preparing VMs for analyzing a malware. Which of the following is NOT a best practice?
What type of file is represented by a colon (:) with a name following it in the Master File Table of NTFS disk?
Which Intrusion Detection System (IDS) usually produces the most false alarms due to the unpredictable behaviors of users and networks?
Where is the default location for Apache access logs on a Linux computer?
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
When using an iPod and the host computer is running Windows, what file system will be used?
What is cold boot (hard boot)?
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like routers?
An investigator is analyzing a checkpoint firewall log and comes across symbols. What type of log is he looking at?

In the following directory listing,
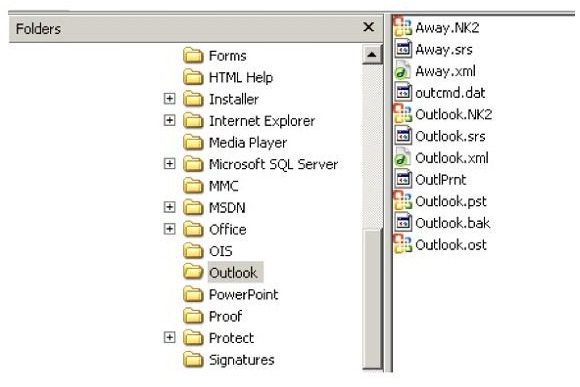
Which file should be used to restore archived email messages for someone using Microsoft Outlook?
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers:
http://172.168.4.131/level/99/exec/show/config
After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
You are contracted to work as a computer forensics investigator for a regional bank that has four 30 TB storage area networks that store customer data.
What method would be most efficient for you to acquire digital evidence from this network?
Netstat is a tool for collecting information regarding network connections. It provides a simple view of TCP and UDP connections, and their state and network traffic statistics. Which of the following commands shows you the TCP and UDP network connections, listening ports, and the identifiers?
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the axfr and ixfr commands using DIG. What is Simon trying to accomplish here?
An International Mobile Equipment Identifier (IMEI) is a 15-digit number that indicates the manufacturer, model type, and country of approval for GSM devices. The first eight digits of an IMEI number that provide information about the model and origin of the mobile device is also known as:



