ECCouncil 312-49v10 - Computer Hacking Forensic Investigator (CHFI-v10)
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
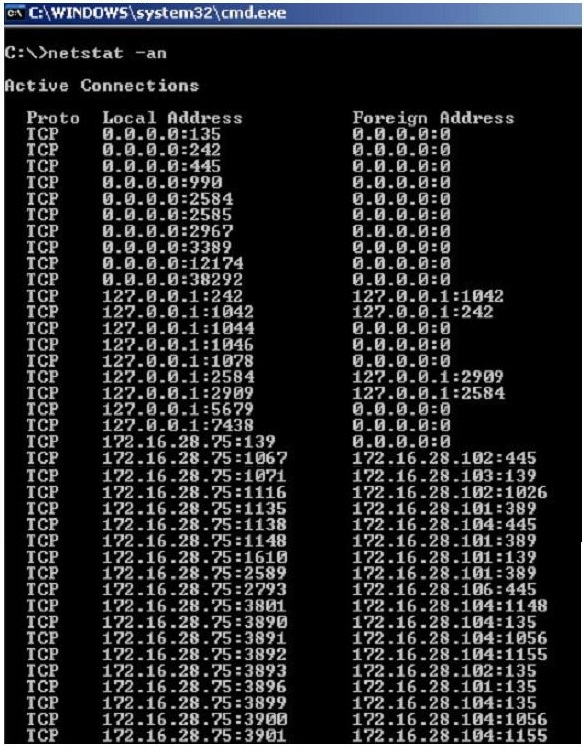
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
Â
Why would you need to find out the gateway of a device when investigating a wireless attack?
The following is a log file screenshot from a default installation of IIS 6.0.
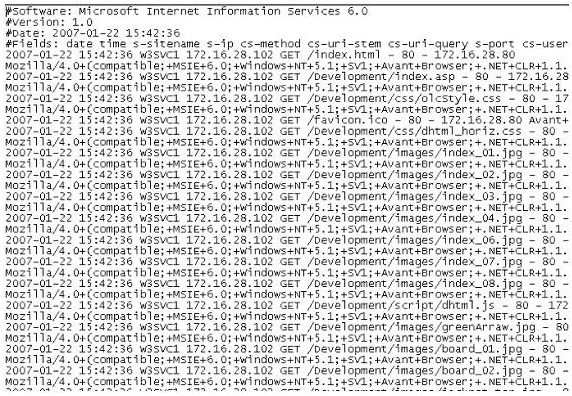
What time standard is used by IIS as seen in the screenshot?
What is the location of the binary files required for the functioning of the OS in a Linux system?
Which of the following acts as a network intrusion detection system as well as network intrusion prevention system?
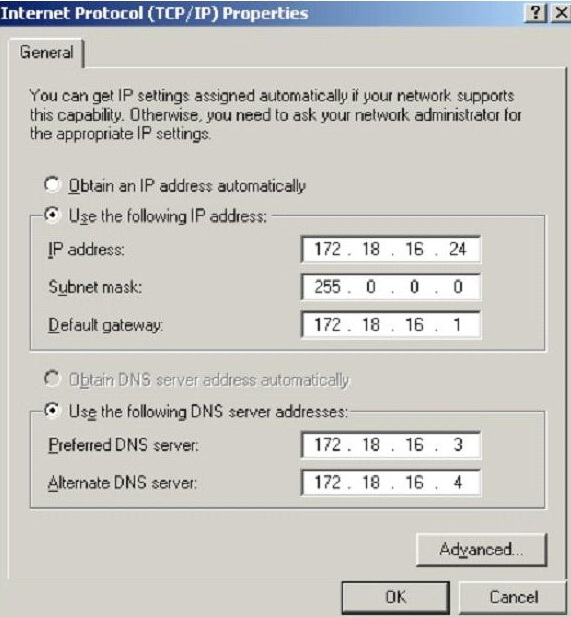
What is the CIDR from the following screenshot?
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed. How many exits should Steven include in his design for the computer forensics lab?
Harold is a computer forensics investigator working for a consulting firm out of Atlanta Georgia. Harold is called upon to help with a corporate espionage case in Miami Florida. Harold assists in the investigation by pulling all the data from the computers allegedly used in the illegal activities. He finds that two suspects in the company where stealing sensitive corporate information and selling it to competing companies. From the email and instant messenger logs recovered, Harold has discovered that the two employees notified the buyers by writing symbols on the back of specific stop signs. This way, the buyers knew when and where to meet with the alleged suspects to buy the stolen material. What type of steganography did these two suspects use?
Which of the following Android libraries are used to render 2D (SGL) or 3D (OpenGL/ES) graphics content to the screen?
Which of the following file system uses Master File Table (MFT) database to store information about every file and directory on a volume?
What must an attorney do first before you are called to testify as an expert?
What is an investigator looking for in the rp.log file stored in a system running on Windows 10 operating system?
BMP (Bitmap) is a standard file format for computers running the Windows operating system. BMP images can range from black and white (1 bit per pixel) up to 24 bit color (16.7 million colors). Each bitmap file contains a header, the RGBQUAD array, information header, and image data. Which of the following element specifies the dimensions, compression type, and color format for the bitmap?
Which one of the following is not a first response procedure?
Smith, an employee of a reputed forensic investigation firm, has been hired by a private organization to investigate a laptop that is suspected to be involved in the hacking of the organization’s DC server. Smith wants to find all the values typed into the Run box in the Start menu. Which of the following registry keys will Smith check to find the above information?



