ECCouncil 312-49v9 - Computer Hacking Forensic Investigator (v9)
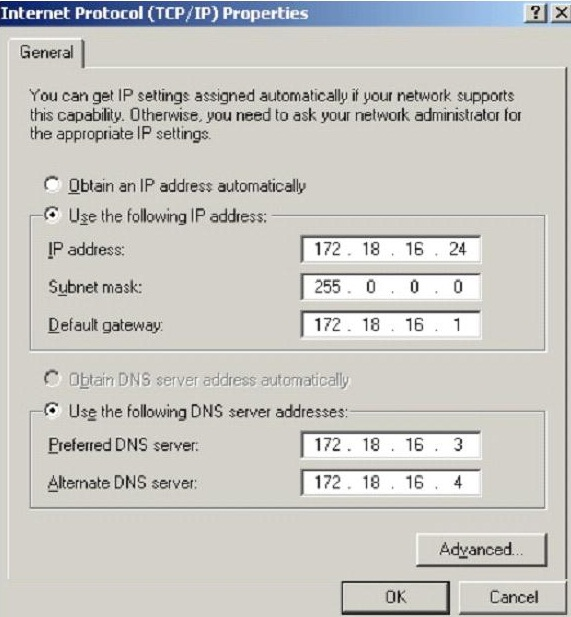
What is the CIDR from the following screenshot?
To which phase of the Computer Forensics Investigation Process does the Planning and Budgeting of a Forensics Lab belong?
Pagefile.sys is a virtual memory file used to expand the physical memory of a computer. Select the registry path for the page file:
Smith, a forensic examiner, was analyzing a hard disk image to find and acquire deleted sensitive files. He stumbled upon a $Recycle.Bin folder in the root directory of the disk. Identify the operating system in use.
Which of the following is an iOS Jailbreaking tool?
Where does Encase search to recover NTFS files and folders?
Data is striped at a byte level across multiple drives, and parity information is distributed among all member drives.
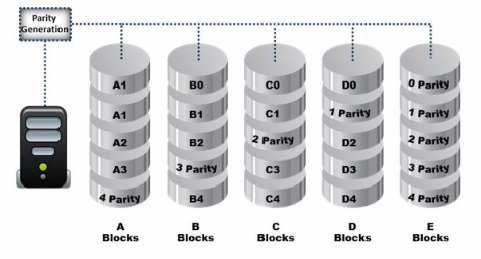
What RAID level is represented here?
What will the following Linux command accomplish?
dd if=/dev/mem of=/home/sam/mem.bin bs=1024
In Steganalysis, which of the following describes a Known-stego attack?
Stephen is checking an image using Compare Files by The Wizard, and he sees the file signature is shown as FF D8 FF E1. What is the file type of the image?
What layer of the OSI model do TCP and UDP utilize?
At what layer does a cross site scripting attack occur on?
If you are concerned about a high level of compression but not concerned about any possible data loss, what type of compression would you use?
Which network attack is described by the following statement? "At least five Russian major banks came under a continuous hacker attack, although online client services were not disrupted. The attack came from a wide-scale botnet involving at least 24,000 computers, located in 30 countries."
Which of the following is a list of recently used programs or opened files?



