ECCouncil 312-49v9 - Computer Hacking Forensic Investigator (v9)
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
What does the superblock in Linux define?
When setting up a wireless network with multiple access points, why is it important to set each access point on a different channel?
Which of the following standard represents a legal precedent sent in 1993 by the Supreme Court of the United States regarding the admissibility of expert witnesses’ testimony during federal legal proceedings?
A small law firm located in the Midwest has possibly been breached by a computer hacker looking to obtain information on their clientele. The law firm does not have any on-site IT employees, but wants to search for evidence of the breach themselves to prevent any possible media attention. Why would this not be recommended?
Which among the following files provides email header information in the Microsoft Exchange server?
The surface of a hard disk consists of several concentric rings known as tracks; each of these tracks has smaller partitions called disk blocks. What is the size of each block?
What type of flash memory card comes in either Type I or Type II and consumes only five percent of the power required by small hard drives?
Why should you never power on a computer that you need to acquire digital evidence from?
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed. How many exits should Steven include in his design for the computer forensics lab?
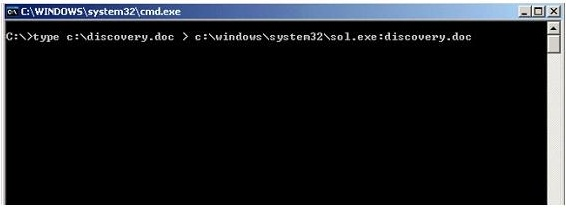
What feature of Windows is the following command trying to utilize?
Who is responsible for the following tasks?
Which of the following files DOES NOT use Object Linking and Embedding (OLE) technology to embed and link to other objects?
You have been called in to help with an investigation of an alleged network intrusion. After questioning the members of the company IT department, you search through the server log files to find any trace of the intrusion. After that you decide to telnet into one of the company routers to see if there is any evidence to be found. While connected to the router, you see some unusual activity and believe that the attackers are currently connected to that router. You start up an ethereal session to begin capturing traffic on the router that could be used in the investigation. At what layer of the OSI model are you monitoring while watching traffic to and from the router?



