ECCouncil 312-50 - Certified Ethical Hacker Exam
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
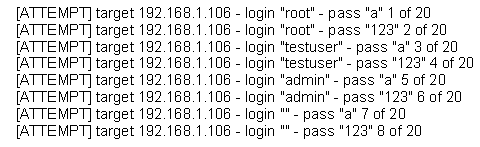
What is most likely taking place?
What information should an IT system analysis provide to the risk assessor?
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
Passive reconnaissance involves collecting information through which of the following?
Which of the following techniques will identify if computer files have been changed?
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
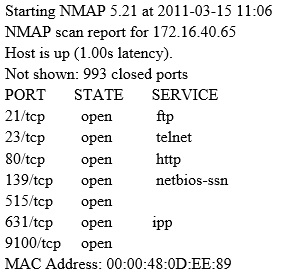
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm's public facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
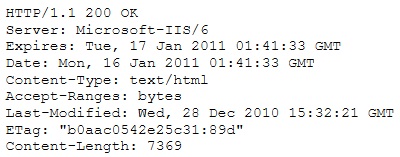
Which of the following is an example of what the engineer performed?
Which of the following is a component of a risk assessment?
Which of the following is considered an acceptable option when managing a risk?



