ECCouncil 312-50v11 - Certified Ethical Hacker Exam (CEH v11)
What kind of detection techniques is being used in antivirus software that identifies malware by collecting data from multiple protected systems and instead of analyzing files locally it’s made on the provider’s environment?
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it? Select the best answers.
Which of the following tactics uses malicious code to redirect users' web traffic?
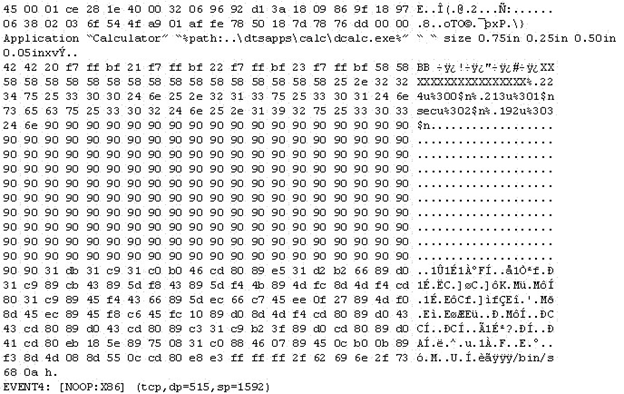
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack.
You also notice "/bin/sh" in the ASCII part of the output.
As an analyst what would you conclude about the attack?
These hackers have limited or no training and know how to use only basic techniques or tools.
What kind of hackers are we talking about?
You just set up a security system in your network. In what kind of system would you find the following string of characters used as a rule within its configuration? alert tcp any any -> 192.168.100.0/24 21 (msg: ““FTP on the network!â€â€;)
What is the main security service a cryptographic hash provides?
What port number is used by LDAP protocol?
An attacker is trying to redirect the traffic of a small office. That office is using their own mail server, DNS server and NTP server because of the importance of their job. The attacker gain access to the DNS server and redirect the direction www.google.com to his own IP address. Now when the employees of the office want to
go to Google they are being redirected to the attacker machine. What is the name of this kind of attack?
As a securing consultant, what are some of the things you would recommend to a company to ensure DNS security?
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
Heather’s company has decided to use a new customer relationship management tool. After performing the appropriate research, they decided to purchase a subscription to a cloud-hosted solution. The only administrative task that Heather will need to perform is the management of user accounts. The provider will take care of the hardware, operating system, and software administration including patching and monitoring. Which of the following is this type of solution?
Due to a slowdown of normal network operations, the IT department decided to monitor internet traffic for all of the employees. From a legal standpoint, what would be troublesome to take this kind of measure?
You have successfully comprised a server having an IP address of 10.10.0.5. You would like to enumerate all machines in the same network quickly.
What is the best Nmap command you will use? A. nmap -T4 -q 10.10.0.0/24
B. nmap -T4 -F 10.10.0.0/24 C. nmap -T4 -r 10.10.1.0/24 D. nmap -T4 -O 10.10.0.0/24
This TCP flag instructs the sending system to transmit all buffered data immediately.



