Cisco 352-011 - Cisco Certified Design Expert Practical Exam
Which two options describe the advantages of using DWDM over traditional optical networks? (Choose two)
Which two options are Loop-Free Alternate design considerations? (Choose two)
You are performing a BGP design review for a service provider that offers MPLS-based services to their end customers. The network is comprised of several PE routers that run iBGP with a pair of route reflectors for all BGP address families. Which two options about the use of Constrained Route Distribution for BGP/MPLS VPNs are true? (Choose two.)
Your client is considering acquiring a new IPv6 address block so that all Ethernet interfaces on the network receive addresses based on their burned-in hardware addresses, with support for 600 VLANs. Which action do you recommend?
Which multicast technology provides a large, many-to-many connectivity for a new application while minimizing load on the existing network infrastructure?
In an OSPF network, users in a particular OSPF non-backbone area are complaining about show access speeds to a shared corporate resource in another OSPF area. Traceroutes show that the users are taking a suboptimal default route to the destinations. Which solution will improve access speed?
Refer to the exhibit,
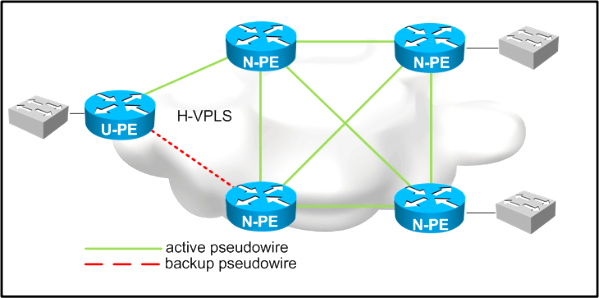
Which two design considerations should be implemented on the pseudowire between N-PE and U-PE routers for a loop-free hierarchical VPLS service? (Choose two)
Which design benefit of Bridge Assurance is true?
A multisite data center network runs OSPF and DWDM point-to-point interfaces for site to-site connectivity. Which method to detect interfaces the fastest?
Which three options are important design functions of IPv6 first-hop security? (Choose three)



