Cisco 400-007 - Cisco Certified Design Expert (CCDE v3.1)
Identity and access management between multiple users and multiple applications has become a mandatory requirement for Company XYZ to fight against ever-increasing cybersecurity threats. To achieve this, federated identity services have been deployed to provide Single Sign-On and Multi-Factor Authentication. Which protocol can be used by Company XYZ to provide authentication and authorization services?
Company XYZ has designed their network to run GRE over IPsec on their Internet-based VPN to connect two sites. Which IPsec tunneling feature can they enable to optimize the data flow while ensuring that the headers contain no duplicate IP addresses?
Which two features are advantages of SD-WAN compared to MPLS-based connectivity? (Choose two.)
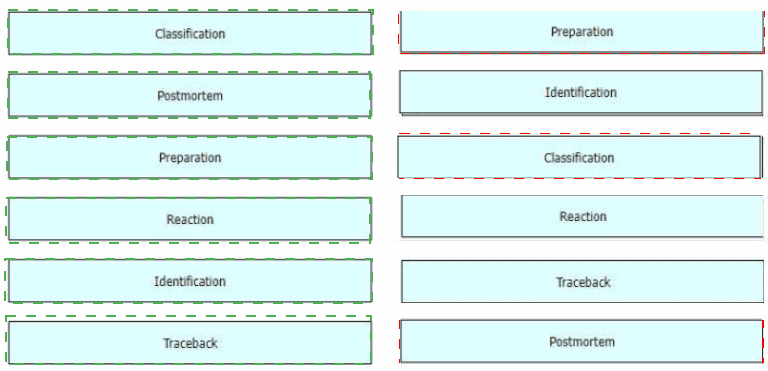
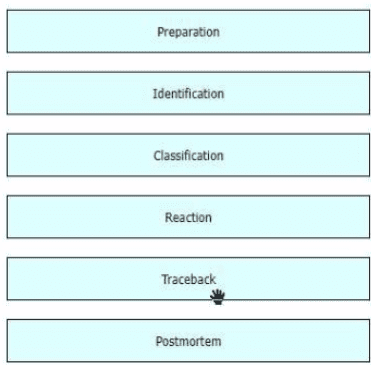
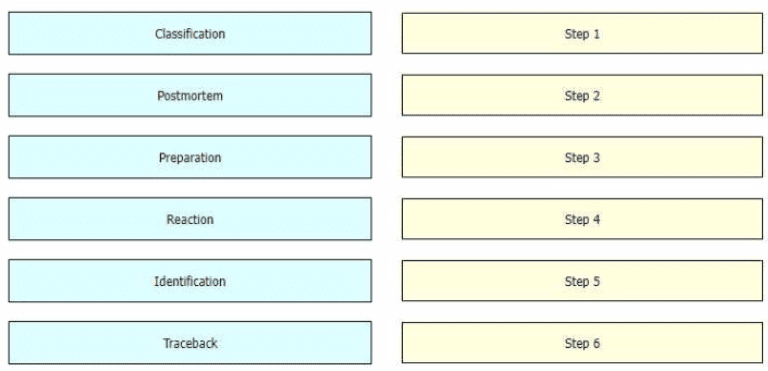
While computer networks and sophisticated applications have allowed individuals to be more productive the need to prepare for security threats has increased dramatically A six-step methodology on security incident handling has been adopted by many organizations including service providers enterprises, and government organizations to ensure that organizations are aware of significant security incidents and act quickly to stop the attacker, minimize damage caused, and prevent follow on attacks or similar incidents in the future Drag and drop the actions on the left to the targets on the right in the correct order.
Which architecture does not require an explicit multicast signaling protocol, such as PIM or P2MP, to signal the multicast state hop-by-hop, but instead uses a link state protocol to advertise the multicast forwarding state?
An Agile for Infrastructure transition often means dismantling traditional IT hierarchies and rebuilding it to align with business objectives and workflows. Organizations are seeing the benefits of using automation tools in the network such as faster, more efficient, and more effective delivery of products and services. Which two components help increase overall productivity and improve company culture? (Choose two.)
A BGP route reflector in the network is taking longer than expected to converge during large network changes. Troubleshooting shows that the router cannot handle all the TCP acknowledgements during route updates. Which action can be performed to tune the device performance?
Which actions are performed at the distribution layer of the three-layer hierarchical network design model? (Choose two)
A business requirement stating that failure of WAN access for dual circuits into an MPLS provider for a Data Centre cannot happen due to related service credits that would need to be paid has led to diversely routed circuits to different points of presence on the provider’s network. What should a network designer also consider as part of the requirement?
SDWAN networks capitalize the usage of broadband Internet links over traditional MPLS links to offer more cost benefits to enterprise customers. However, due to the insecure nature of the public Internet, it is mandatory to use encryption of traffic between any two SDWAN edge devices installed behind NAT gateways. Which overlay method can provide optimal transport over unreliable underlay networks that are behind NAT gateways?