Cisco 400-007 - Cisco Certified Design Expert (CCDE v3.1)
Which two statements describe network automation and network orchestration? (Choose two.)
A European government passport agency considers upgrading its IT systems to increase performance and workload flexibility in response to constantly changing requirements. The budget manager wants to reduce capital expenses and IT staff and must adopt the lowest-cost technology. Which technology choice is suitable?
The major business applications of an enterprise are largely monolithic and hard-coded. As part of a major modernization and overhaul of the applications, the goal is to move to a modular and containerized application architecture model. At the same time, decoupling from the hardware is desired to move to an on-demand provisioning. However, the CyberOps team mandated that the final architecture must provide the same security levels as an air-gapped data center. Which cloud architecture meets these requirements?
Company XYZ is running a redundant private WAN network using OSPF as the underlay protocol. The current design accommodates for redundancy in the network, but it is taking over 30 seconds for the network to reconverge upon failure. Which technique can be implemented in the design to detect such a failure in a subsecond?
Company XYZ is migrating their existing network to IPv6. Some access layer switches do not support IPv6, while core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used?
Cost is often one of the motivators for a business to migrate from a traditional network to a software-defined network. Which design decision is directly influenced by CAPEX drivers?
Refer to the table.
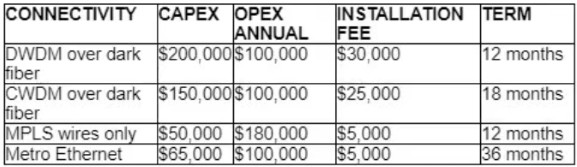
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads. Which transport technology provides the best ROI based on cost and flexibility?
Company XYZ wants to use the FCAPS ISO standard for network management design. The focus of the design should be to monitor and keep track of any performance issues by continuously collecting and analyzing statistical information to monitor, correct, and optimize any reduced responsiveness across the network. Which layer accomplishes this design requirement?
What is a characteristic of a secure cloud architecture model?
Which two mechanisms avoid suboptimal routing in a network with dynamic mutual redistribution between multiple OSPFv2 and EIGRP boundaries? (Choose two.)



