CompTIA CAS-004 - CompTIA SecurityX Certification Exam
As part of the customer registration process to access a new bank account, customers are required to upload a number of documents, including their passports and driver’s licenses. The process also requires customers to take a current photo of themselves to be compared against provided documentation.
Which of the following BEST describes this process?
Which of the following agreements includes no penalties and can be signed by two entities that are working together toward the same goal?
A security analyst observes the following while looking through network traffic in a company's cloud log:
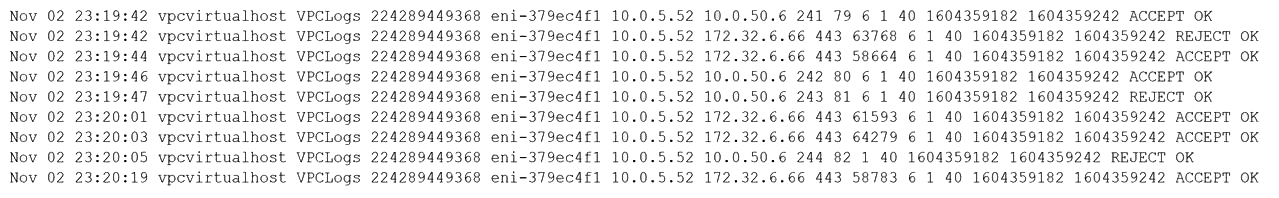
Which of the following steps should the security analyst take FIRST?
A security architect is given the following requirements to secure a rapidly changing enterprise with an increasingly distributed and remote workforce
• Cloud-delivered services
• Full network security stack
• SaaS application security management
• Minimal latency for an optimal user experience
• Integration with the cloud 1AM platform
Which of the following is the BEST solution?
A company’s product site recently had failed API calls, resulting in customers being unable to check out and purchase products. This type of failure could lead to the loss of customers and damage to the company’s reputation in the market.
Which of the following should the company implement to address the risk of system unavailability?
A security consultant needs to protect a network of electrical relays that are used for monitoring and controlling the energy used in a manufacturing facility.
Which of the following systems should the consultant review before making a recommendation?
A host on a company’s network has been infected by a worm that appears to be spreading via SMB. A security analyst has been tasked with containing the incident while also maintaining evidence for a subsequent investigation and malware analysis.
Which of the following steps would be best to perform FIRST?
A large number of emails have been reported, and a security analyst is reviewing the following information from the emails:
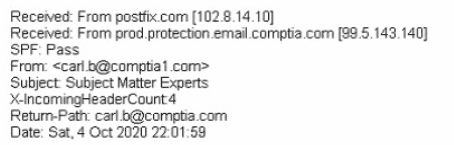
As part of the image process, which of the following is the FIRST step the analyst should take?
The goal of a Chief information Security Officer (CISO) providing up-to-date metrics to a bank’s risk committee is to ensure:
A security analyst is reading the results of a successful exploit that was recently conducted by third-party penetration testers. The testers reverse engineered a privileged executable. In the report, the planning and execution of the exploit is detailed using logs and outputs from the test However, the attack vector of the exploit is missing, making it harder to recommend remediation’s. Given the following output:
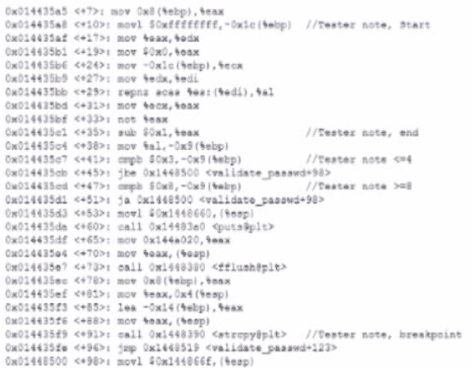
The penetration testers MOST likely took advantage of:
A review of the past year’s attack patterns shows that attackers stopped reconnaissance after finding a susceptible system to compromise. The company would like to find a way to use this information to protect the environment while still gaining valuable attack information.
Which of the following would be BEST for the company to implement?
A threat analyst notices the following URL while going through the HTTP logs.
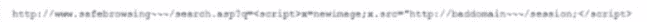
Which of the following attack types is the threat analyst seeing?
A municipal department receives telemetry data from a third-party provider The server collecting telemetry sits in the municipal departments screened network and accepts connections from the third party over HTTPS. The daemon has a code execution vulnerability from a lack of input sanitization of out-of-bound messages, and therefore, the cybersecurity engineers would like to Implement nsk mitigations. Which of the following actions, if combined, would BEST prevent exploitation of this vulnerability? (Select TWO).
A company requires a task to be carried by more than one person concurrently. This is an example of:
A security analyst is trying to identify the source of a recent data loss incident. The analyst has reviewed all the for the time surrounding the identified all the assets on the network at the timeof the data loss. The analyst suspects the key to finding the source was obfuscated in an application. Which of the following tools should the analyst use NEXT?



