CompTIA CAS-005 - CompTIA SecurityX Certification Exam
A company wants to perform threat modeling on an internally developed, business-critical application. The Chief Information Security Officer (CISO) is most concerned that the application should maintain 99.999% availability and authorized users should only be able to gain access to data they are explicitly authorized to view. Which of the following threat-modeling frameworks directly addresses the CISO's concerns about this system?
A security analyst is troubleshooting the reason a specific user is having difficulty accessing company resources The analyst reviews the following information:
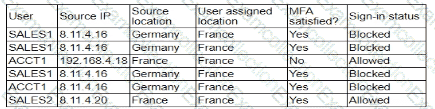
Which of the following is most likely the cause of the issue?
A company that relies on an COL system must keep it operating until a new solution is available Which of the following is the most secure way to meet this goal?
A security administrator is reviewing the following code snippet from a website component:

A review of the inc.tmp file shows the following:
Which of the following is most likely the reason for inaccuracies?
A hospital provides tablets to its medical staff to enable them to more quickly access and edit patients' charts. The hospital wants to ensure that if a tablet is identified as lost or stolen and a remote command is issued, the risk of data loss can be mitigated within seconds. The tablets are configured as follows:
• Full disk encryption is enabled.
• "Always On" corporate VPN is enabled.
• eFuse-backed keystore is enabled.
• Wi-Fi 6 is configured with SAE.
• Location services is disabled.
• Application allow list is unconfigured.
Assuming the hospital policy cannot be changed, which of the following is the best way to meet the hospital's objective?
An organization that performs real-time financial processing is implementing a new backup solution. Given the following business requirements:
The backup solution must reduce the risk of potential backup compromise.
The backup solution must be resilient to a ransomware attack.
The time to restore from backups is less important than backup data integrity.
Multiple copies of production data must be maintained.
Which of the following backup strategies best meets these requirements?
Users are willing passwords on paper because of the number of passwords needed in an environment. Which of the following solutions is the best way to manage this situation and decrease risks?
A security team determines that the most significant risks within the pipeline are:
• Unauthorized code changes
• The current inability to perform independent verification of software modules
Which of the following best addresses these concerns?
Which of the following includes best practices for validating perimeter firewall configurations?
Which of the following most likely explains the reason a security engineer replaced ECC with a lattice-based cryptographic technique?



