CyberArk CAU302 - CyberArk Defender + Sentry
An auditor initiates a LIVE monitoring session to PSM server to view an ongoing LIVE session. When the
auditor’s machine makes an RDP connection the PSM server, which user will be used?
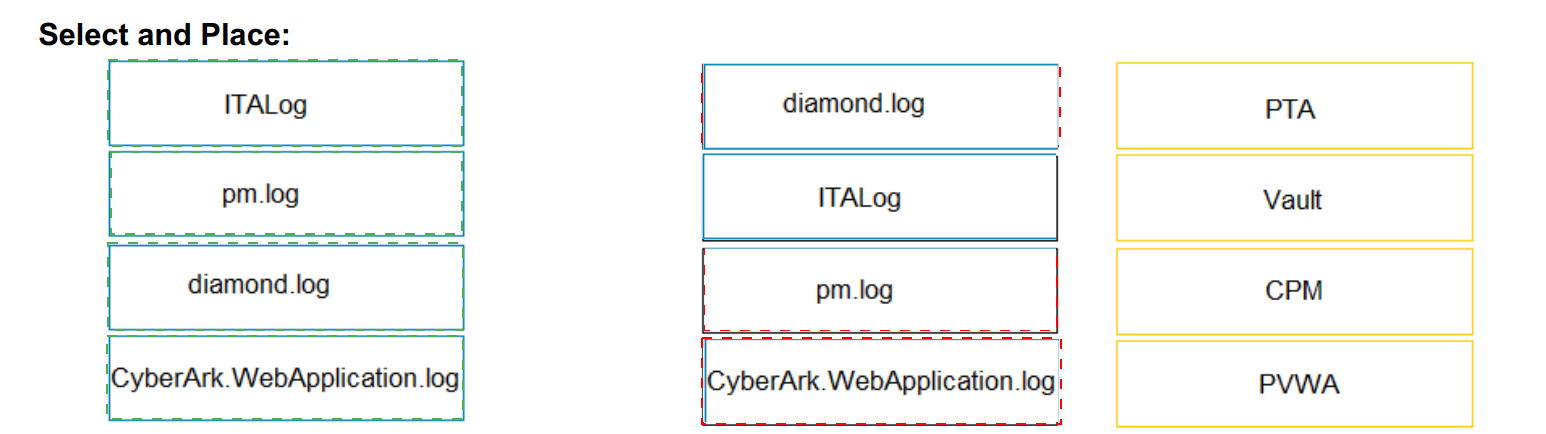
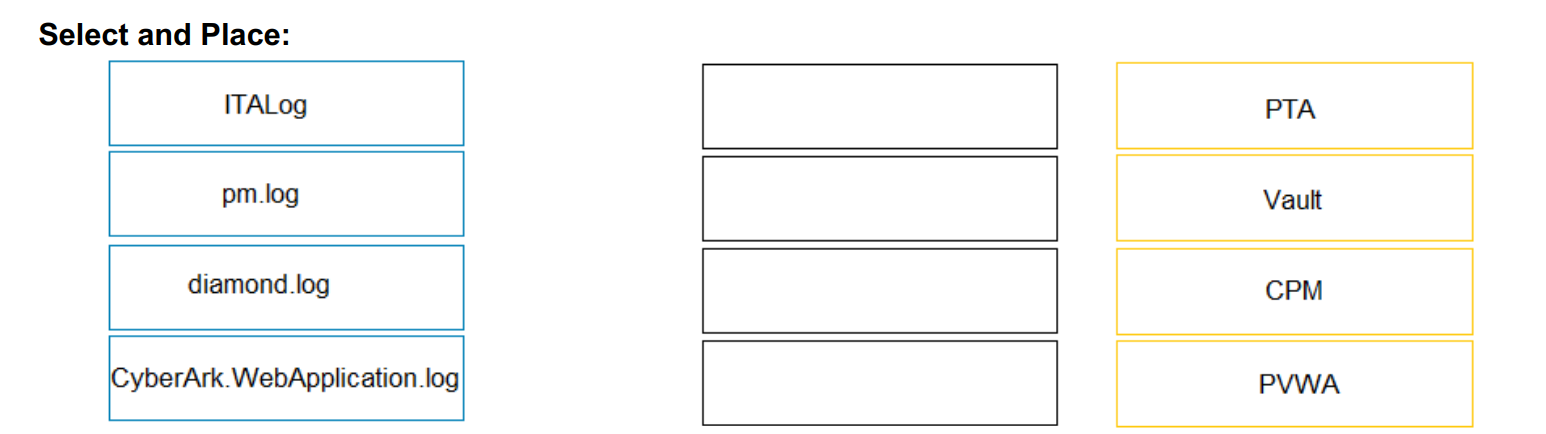
Match the log file name with the CyberArk Component that generates the log.
According to the default web options settings, which group grants access to the reports page?
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault.
The PSM requires the Remote Desktop Web Access role service.
When managing SSH keys. CPM automatically pushes the Public Key to the target system.
If a password is changed manually on a server, bypassing the CPM, how would you configure the account so
that the CPM could resume management automatically?
tsparm.ini is the main configuration file for the vault.
It is possible to restrict the time of day. or day of week that a change process can occur
Which report shows the accounts that are accessible to each user?