ISC CC - CC - Certified in Cybersecurity
Which of the following is a systematic approach to protecting against cyber threats that involves a continuous cycle of identifying, assessing and prioritizing risks and implementing measures to reduce or eliminate those risks?
Which ensure maintaining business operations during or after an incident
Exhibit.
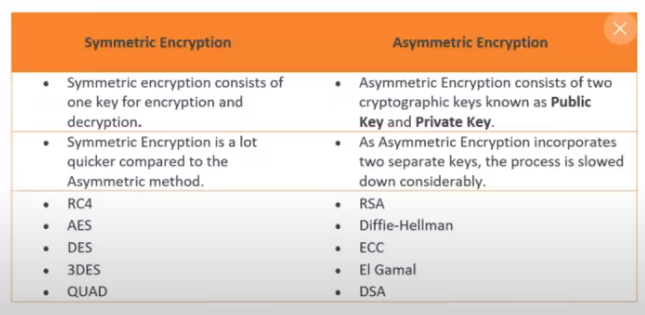
How many keys would be required to support 50 users in an asymmetric cryptography system?
Which Prevents Threat
Part of a zero-trust strategy that breaks LANs into very small and highly localized zones using firewalls.
Incident management is also known as
What is the potential impact of an IPSec reply attack
Mark has purchased a MAC LAPTOP. He is scared of losing his screen and planning to buy an insurance policy. So, which risk management strategy is?
Which of the following is NOT one of the three main components of a sql database?
Which of the following is very likely to be used in a disaster recovery (DR) effort?



