Isaca CRISC - Certified in Risk and Information Systems Control
Which of the following is the BEST way to support communication of emerging risk?
Which of the following is the PRIMARY purpose of creating and documenting control procedures?
Which of the following should be the MAIN consideration when validating an organization's risk appetite?
An upward trend in which of the following metrics should be of MOST concern?
Which of the following is MOST important for a risk practitioner to ensure once a risk action plan has been completed?
Which of the following is MOST important to review when an organization needs to transition the majority of its employees to remote work during a crisis?
Which of the following would be the BEST way for a risk practitioner to validate the effectiveness of a patching program?
Which of the following BEST enables a risk practitioner to identify the consequences of losing critical resources due to a disaster?
An organization has engaged a third party to provide an Internet gateway encryption service that protects sensitive data uploaded to a cloud service. This is an example of risk:
The PRIMARY focus of an ongoing risk awareness program should be to:
Which of the following is MOST important to promoting a risk-aware culture?
Which of the following would provide the BEST evidence of an effective internal control environment/?
When reviewing a risk response strategy, senior management's PRIMARY focus should be placed on the:
Which of the following activities BEST facilitates effective risk management throughout the organization?
Risk appetite should be PRIMARILY driven by which of the following?
Which of the following should be implemented to BEST mitigate the risk associated with infrastructure updates?
Because of a potential data breach, an organization has decided to temporarily shut down its online sales order system until sufficient controls can be implemented. Which risk treatment has been selected?
Which of the following BEST enables the timely detection of changes in the security control environment?
An organization has allowed several employees to retire early in order to avoid layoffs Many of these employees have been subject matter experts for critical assets Which type of risk is MOST likely to materialize?
Which of the following is the MOST effective way to assess the risk associated with outsourcing IT processes?
An organization is considering allowing users to access company data from their personal devices. Which of the following is the MOST important factor when assessing the risk?
Which of the following is the MOST important reason to validate that risk responses have been executed as outlined in the risk response plan''
Which of the following would BEST help an enterprise prioritize risk scenarios?
Which of the following is the BEST course of action when an organization wants to reduce likelihood in order to reduce a risk level?
Which of the following is the BEST key performance indicator (KPI) to measure how effectively risk management practices are embedded in the project management office (PMO)?
Which of the following activities should be performed FIRST when establishing IT risk management processes?
A risk assessment has revealed that the probability of a successful cybersecurity attack is increasing. The potential loss could exceed the organization's risk appetite. Which of the following ould be the MOST effective course of action?
An IT department has provided a shared drive for personnel to store information to which all employees have access. Which of the following parties is accountable for the risk of potential loss of confidential information?
When reporting risk assessment results to senior management, which of the following is MOST important to include to enable risk-based decision making?
An organization has updated its acceptable use policy to mitigate the risk of employees disclosing confidential information. Which of the following is the BEST way to reinforce the effectiveness of this policy?
Which of the following is the PRIMARY accountability for a control owner?
Which of the following will BEST help to improve an organization's risk culture?
Which of the following is MOST important when defining controls?
The PRIMARY purpose of IT control status reporting is to:
Which of the following is the PRIMARY objective of providing an aggregated view of IT risk to business management?
An organization has introduced risk ownership to establish clear accountability for each process. To ensure effective risk ownership, it is MOST important that:
An organization that has been the subject of multiple social engineering attacks is developing a risk awareness program. The PRIMARY goal of this program should be to:
Which of the following presents the GREATEST risk to change control in business application development over the complete life cycle?
What is the PRIMARY reason an organization should include background checks on roles with elevated access to production as part of its hiring process?
Which of the following statements BEST describes risk appetite?
Which of the following BEST enables detection of ethical violations committed by employees?
What should a risk practitioner do FIRST when a shadow IT application is identified in a business owner's business impact analysis (BIA)?
Which of the following should be the PRIMARY consideration when implementing controls for monitoring user activity logs?
Which of the following is MOST important for maintaining the effectiveness of an IT risk register?
Which of the following is the MOST important characteristic of an effective risk management program?
Which of the following is the BEST way for a risk practitioner to present an annual risk management update to the board''
Which of the following is MOST helpful to ensure effective security controls for a cloud service provider?
During a routine check, a system administrator identifies unusual activity indicating an intruder within a firewall. Which of the following controls has MOST likely been compromised?
Which of the following is MOST important to communicate to senior management during the initial implementation of a risk management program?
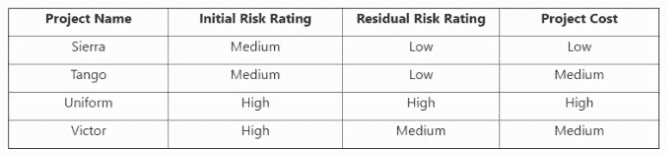
What can be determined from the risk scenario chart?