CompTIA CS0-002 - CompTIA CySA+ Certification Exam (CS0-002)
A security analyst performed a targeted system vulnerability scan to obtain critical information. After the output result, the analyst used the OVAL XML language to review and calculate the discovered risk. Which of the following types of scans did the security analyst perform?
A vulnerability scanner has identified an out-of-support database software version running on a server. The software update will take six to nine months to complete. The management team has agreed to a one-year extended support contract with the software vendor. Which of the following BEST describes the risk treatment in this scenario?
A security analyst is reviewing vulnerability scans from an organization's internet-facing web services. The following is from an output file called ssl-test_webapps.comptia.org:
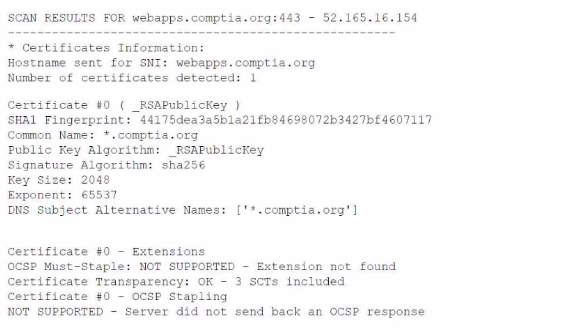
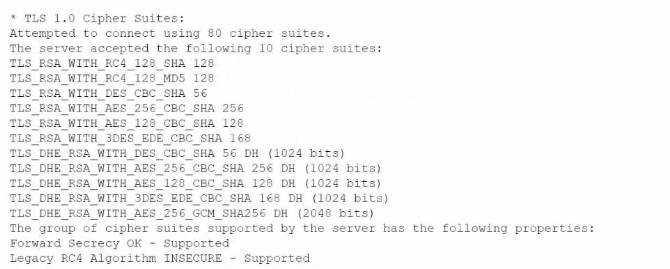
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
During a routine review of service restarts a security analyst observes the following in a server log:
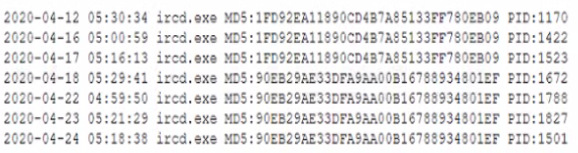
Which of the following is the GREATEST security concern?
A company wants to configure the environment to allow passive network monitonng. To avoid disrupting the sensitive network, which of the following must be supported by the scanner's NIC to assist with the company's request?
A security analyst is reviewing the following Internet usage trend report:
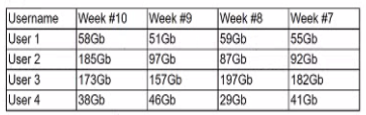
Which of the following usernames should the security analyst investigate further?
A security analyst is concerned about sensitive data living on company file servers following a zero-day attack that nearly resulted in a breach of millions of customer records. The after action report indicates a lack of controls around the file servers that contain sensitive data. Which of the following DLP considerations would best help the analyst to classify and address the sensitive data on the file servers?
A SIEM analyst receives an alert containing the following URL:

Which of the following BEST describes the attack?
A new government regulation requires that organizations only retain the minimum amount of data on a person to perform the organization's necessary activities. Which of the following techniques would help an organization comply with this new regulation?
While going through successful malware cleanup logs, an analyst notices an old worm that has been replicating itself across the company's network Reinfection of the malware can be prevented with a patch; however, most of the affected systems cannot be patched because the patch would make the system unstable. Which of the following should the analyst recommend to best prevent propagation of the malware throughout the network?



