Swift CSP-Assessor - Customer Security Programme Assessor Certification(CSPAC)
The internet connectivity restriction control prevents having internet access on any CSCE m-scope components.

TRUE
FALSE
The Answer Is:
BExplanation:
This question addresses the internet connectivity restriction control and its application to CSCF in-scope components. Let’s verify this against Swift CSP guidelines.
Step 1: Understand the Internet Connectivity Restriction Control
TheSwift Customer Security Controls Framework (CSCF) v2024, underControl 2.6: Internet Accessibility Restriction, mandates that in-scope components (e.g., Swift messaging interfaces, communication interfaces) must not have direct internet access to prevent exposure to external threats. However, this control allows for exceptions under specific conditions.
Step 2: Analyze the Statement
The statement claims that the internet connectivity restriction control “prevents having internet access on any CSCF in-scope components.†The key is to determine if this is an absolute prohibition or if exceptions exist.
Step 3: Evaluate Against CSCF Guidelines
Control 2.6: Internet Accessibility Restrictionrequires that Swift-related systems be isolated from the internet to minimize attack surfaces. This includes components like messaging interfaces (e.g., Alliance Access) and communication interfaces (e.g., SNL).
However, theCSCF v2024andSwift CSP FAQallow for controlled internet access under specific circumstances, such as:
Use of secure tunnels (e.g., VPNs) or proxies for authorized management purposes.
Temporary access for software updates or patches, provided it is tightly controlled and monitored (perControl 6.1: Security Event Logging).
The control does not impose an absolute ban but requires that any internet access be restricted, audited, and justified. Thus, the statement that it “prevents having internet access on any CSCF in-scope components†is too absolute.
Step 4: Conclusion and Verification
The statement isFALSEbecause, while internet access is heavily restricted for in-scope components, it is not entirely prevented under all circumstances (e.g., controlled access for maintenance). This aligns with the flexible yet secure approach of theCSCF v2024.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.6: Internet Accessibility Restriction.
Swift CSP FAQ, Section: Internet Access Exceptions.
What is the purpose of a SWIFT HSM? (Select the correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
To encrypt the database of the messaging interface
To store PKI certificates
To connect to the SWIFT Secure IP Network (SIPN)
To format the FIN MT messages
The Answer Is:
BExplanation:
A Hardware Security Module (HSM) in the SWIFT context is a physical or virtual device used to manage cryptographic keys and perform security operations. Its purpose is critical to ensuring the integrity and confidentiality of SWIFT transactions. Let’s evaluate each option:
•Option A: To encrypt the database of the messaging interface
This is incorrect. While HSMs can perform encryption, their primary role in the SWIFT ecosystem is not to encrypt databases of messaging interfaces (e.g., Alliance Access). Database encryption is typically handled by the institution’s own security measures or software, not the HSM. The CSCF focuses on HSMs for key management and message security, not database-level encryption (e.g., Control "1.1 SWIFT Environment Protection").
•Option B: To store PKI certificates
This is correct. The SWIFT HSM is used to securely store and manage Public Key Infrastructure (PKI) certificates, which are essential for authentication, message signing, and encryption within the SWIFT network. SWIFT uses PKI for role-based access control and to secure communications over SWIFTNet. The HSM ensures that these certificates are protected against unauthorized access and tampering, aligning with CSCF Control "1.3 Cryptographic Failover." For example, in Alliance Gateway setups, the HSM stores SWIFTNet PKI certificates used for secure message transmission.
•Option C: To connect to the SWIFT Secure IP Network (SIPN)
This is incorrect. Connection to the SIPN is managed by components like SwiftNet Link (SNL) and VPN boxes, not the HSM. The HSM’s role is security-focused, handling cryptographic operations, not network connectivity. CSCF Control "1.1" specifies that connectivity is achieved through network components, while the HSM supports security within that environment.
•Option D: To format the FIN MT messages
This is incorrect. Message formatting (e.g., creating FIN MT messages like MT103) is handled by messaging interfaces like Alliance Access or Alliance Gateway, not the HSM. The HSM’s function is limited to cryptographic tasks, such as signing and verifying messages after they are formatted, as per CSCF Control "2.1 Internal Data Transmission Security."
Summary of Correct Answer:
The primary purpose of a SWIFT HSM is to store PKI certificates, ensuring secure cryptographic operations for SWIFT transactions.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 1.3 mandates the use of HSMs for cryptographic failover and certificate management.
•SWIFT Security Guidelines: HSMs are described as key management devices for PKI certificates in SWIFTNet communications.
•Alliance Gateway Documentation: Details the HSM’s role in storing and managing PKI certificates for secure message processing.
The Alliance Web Platform Administrator uses both the GUI and command line to perform configuration and monitoring tasks on AWP SE.

TRUE
FALSE
The Answer Is:
BExplanation:
This question pertains to the Alliance Web Platform (AWP) Single Edition (SE) Administrator’s capabilities:
Step 1: AWP SE Overview
AWP SE is a web-based interface for managing SWIFT services (e.g., Alliance Lite2, monitoring tools). It’s primarily GUI-driven, unlike Alliance Access, which supports command-line operations.
The Swift HSM boxes:

Are located at the network partner premises and managed by Swift
Are located at the Swift user premises and managed by Swift
Are located at the Swift user premises and managed by the Swift user
Are located at the network partner premises and managed by Swift the network partner
The Answer Is:
CExplanation:
This question concerns the location and management of Swift HSM boxes, which are critical for secure key management.
Step 1: Understand the Role of Swift HSM
The Hardware Security Module (HSM) in the Swift environment is used to store and manage cryptographic keys, as perControl 2.5B: Cryptographic Key Managementof theCSCF v2024. The HSM ensures the security of Swift transactions by protecting private keys.
Step 2: Evaluate Each Option
A. Are located at the network partner premises and managed by SwiftNetwork partners (e.g., service providers) may host connectivity infrastructure, but HSMs are typically located at the user’s premises for direct control, as perSwift Security Best Practices. Swift does not manage user HSMs; users are responsible for their operation.Conclusion: This is incorrect.
B. Are located at the Swift user premises and managed by SwiftWhile HSMs are located at the user’s premises, Swift does not manage them. Users are responsible for HSM management, as outlined inControl 2.5B, which requires users to secure and maintain their HSMs.Conclusion: This is incorrect.
C. Are located at the Swift user premises and managed by the Swift userTheCSCF v2024andSwift HSM Deployment Guidespecify that HSMs are deployed at the Swift user’s premises to ensure local control and security. Users are responsible for managing and maintaining the HSM, including key generation and backups, as part of their compliance obligations.Conclusion: This is correct.
D. Are located at the network partner premises and managed by Swift the network partnerHSMs are not managed by network partners or Swift. Users retain control, and network partners only facilitate connectivity, not HSM management.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The verified answer isC, as it accurately reflects the standard deployment and management model for Swift HSMs, consistent with Swift CSP documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.5B: Cryptographic Key Management.
Swift HSM Deployment Guide, Section: Installation and Management.
Swift Security Best Practices, Section: HSM Location and Control.
As a Swift CSP Certified Assessor. Swift contacted me to provide evidence on an assessment I have performed. This is required to support their quality assurance validation process. Is it allowed?

Yes, one of the obligations of the certification programme is that quality assessment can be performed by Swift
No, it's confidential
The Answer Is:
AExplanation:
This question addresses the obligations of a Swift CSP Certified Assessor regarding the provision of evidence to Swift for quality assurance purposes.
Step 1: Understand the Role of a Swift CSP Certified Assessor
A Swift CSP Certified Assessor is an independent professional or entity authorized to conduct CSP assessments under theIndependent Assessment Framework. The certification program, managed by Swift, includes specific obligations to ensure the integrity and quality of assessments.
Step 2: Analyze the Request for Evidence
Swift has contacted the assessor to provide evidence from an assessment to support their quality assurance validation process. This request implies a review of the assessor’s work to ensure compliance with CSP standards.
TheSwift CSP Assessor Certification Program Guidelinesstate that certified assessors are obligated to cooperate with Swift’s quality assurance processes. This includes providingevidence (e.g., assessment reports, workpapers) upon request to verify the accuracy and adherence to methodology, as part of Swift’s oversight.
Confidentiality is a concern, but theCSCF v2024andAssessor Certification Programclarify that assessors must share evidence with Swift under a non-disclosure agreement (NDA) or similar confidentiality framework, ensuring data protection while allowing validation.
Step 3: Evaluate Each Option
A. Yes, one of the obligations of the certification programme is that quality assessment can be performed by SwiftTheSwift CSP Assessor Certification Program Guidelinesexplicitly outline that Swift may conduct quality assessments, and assessors must provide evidence to support this process. This is a contractual obligation of certification, aligning with Swift’s responsibility to maintain CSP integrity.Conclusion: This is correct.
B. No, it's confidentialWhile confidentiality is critical (protected underControl 2.3: System Access Controland Swift’s privacy policies), the certification program requires assessors to share evidence with Swift for quality assurance, subject to confidentiality agreements. Refusing to provide evidence would breach the assessor’s obligations.Conclusion: This is incorrect.
Step 4: Conclusion and Verification
The answer isA, as theSwift CSP Assessor Certification Programmandates that certified assessors must support Swift’s quality assurance validation by providing evidence, balancing confidentiality with compliance oversight.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.3: System Access Control.
Swift CSP Assessor Certification Program Guidelines, Section: Obligations and Quality Assurance.
Swift Independent Assessment Framework, Section: Assessor Responsibilities.
Select the correct statement about Alliance Gateway.

It is used to exchange messages over the Swift network
It is used to create messages to send over the Swift network
The Answer Is:
AExplanation:
This question revisits the role of the Swift Alliance Gateway (SAG), similar to Question 6, but with different statements.
Step 1: Recap the Role of Alliance Gateway
The Swift Alliance Gateway (SAG) is a connectivity and security layer that facilitates interaction with the Swift network, as detailed in theSwift Alliance Gateway User Guideand referenced inControl 1.1: Swift Environment Protectionof theCSCF v2024.
Step 2: Evaluate Each Option
A. It is used to exchange messages over the Swift networkThe SAG acts as a gateway to concentrate and securely route SwiftNet traffic, enabling the exchange of messages over the Swift network. It handles connectivity, security (e.g., PKI), and message routing, as confirmed in theSwift Alliance Gateway Technical Documentation. This aligns with its role in the Swift ecosystem.Conclusion: This is correct.
B. It is used to create messages to send over the Swift networkAs noted in Question 6, the SAG does not create messages. Message creation is handled by applications like Alliance Access or Entry. The SAG’s role is to route and secure messages, not generate them, per theSwift Alliance Gateway User Guide.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The correct statement isA, as the Alliance Gateway’s primary function is to facilitate the secure exchange of messages over the Swift network, consistent with Swift CSP documentation.
References
Swift Alliance Gateway User Guide, Section: Functionality Overview.
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Alliance Gateway Technical Documentation, Section: Message Routing.
In the illustration, identify which components are in scope of the CSCF? (Choose all that apply.)

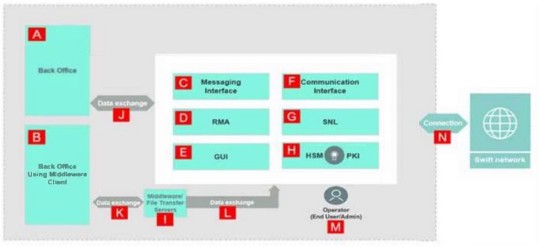
Components A, B, K
Components J, K, I
Components F, G, H
Components C, E, M
The Answer Is:
C, DExplanation:
The Swift Customer Security Controls Framework (CSCF) defines the scope of components that must comply with its security controls. This scope is detailed in theCSCF v2024(and prior versions like CSCF v2023), which specifies that the CSCF applies to systems directly involved in the Swift messaging and connectivity ecosystem. Let’s analyze the diagram to identify which components fall within this scope.
Step 1: Understand the Scope of CSCF
According to theSwift Customer Security Controls Framework (CSCF) v2024, the scope includes:
Swift messaging interfaces(e.g., Alliance Access/Entry, RMA).
Communication interfacesto the Swift network (e.g., SNL, HSM, PKI).
Operator systemsdirectly interacting with Swift components (e.g., GUIs, admin/operator workstations).
Middlewareor connectors directly facilitating Swift message flows.Systems that are not directly involved in Swift messaging or connectivity (e.g., back-office systems, general-purpose servers) are typically out of scope unless they pose a direct risk to the Swift environment.
Step 2: Analyze the Diagram and Identify Components
The diagram includes the following labeled components:
A. Back Office: A system for back-office operations, not directly part of Swift messaging.
B. Back Office Using Middleware Client: A back-office system with middleware for data exchange.
C. Messaging Interface: Likely a Swift messaging interface (e.g., Alliance Access).
D. RMA: Relationship Management Application, a Swift component for managing messaging relationships.
E. GUI: Graphical User Interface for operators to interact with the messaging interface.
F. Communication Interface: Interface for connecting to the Swift network.
G. SNL: SwiftNet Link, a communication layer for Swift connectivity.
H. HSM & PKI: Hardware Security Module and Public Key Infrastructure, used for secure Swift connectivity.
I. Middleware File Transfer Servers: Servers facilitating data exchange between back-office and Swift systems.
J, K, L. Data Exchange Paths: Represent data flows between systems (not components themselves).
M. Operator (End User): The operator’s workstation interacting with the Swift GUI.
N. Connector: The connection point to the Swift network.
Step 3: Evaluate Each Option Against CSCF Scope
A. Components A, B, K
A (Back Office): Back-office systems are not in scope unless they directly process Swift messages. The CSCF focuses on Swift-specific infrastructure, and back-office systems are typically considered out of scope unless they pose a direct risk (e.g., via middleware).
B (Back Office Using Middleware Client): While this system uses middleware to exchange data with Swift components, it is still a back-office system, not a core Swift component. The middleware itself (I) may be in scope, but the client (B) is not.
K (Data Exchange Path): This is a data flow, not a component, and thus not directly in scope.Conclusion: This option is incorrect.
B. Components J, K, I
J, K (Data Exchange Paths): These are data flows, not components, and are not directly in scope.
I (Middleware File Transfer Servers): Middleware that facilitates Swift message flows (e.g., between back-office and messaging interface) can be in scope if it directlyprocesses or transmits Swift messages. PerControl 1.1: Swift Environment Protection, middleware in the Swift data flow must be secured, making it in scope. However, this option pairs I with J and K, which are not components.Conclusion: This option is incorrect due to J and K, though I alone would be in scope.
C. Components F, G, H
F (Communication Interface): This is the interface connecting to the Swift network, clearly in scope perControl 1.1.
G (SNL): SwiftNet Link is a core communication component for Swift connectivity, in scope perControl 1.1.
H (HSM & PKI): HSM and PKI are critical for secure Swift connectivity, in scope perControl 1.1.Conclusion: This option is correct.
D. Components C, E, M
C (Messaging Interface): This is a core Swift component (e.g., Alliance Access), in scope perControl 1.1.
E (GUI): The GUI used by operators to interact with the messaging interface is in scope, as specified inControl 1.2: Logical Access Control, which includes operator systems.
M (Operator End User): The operator’s workstation is in scope as it directly interacts with Swift systems, perControl 1.2.Conclusion: This option is correct.
Step 4: Conclusion and Verification
The components in scope of the CSCF are those directly involved in Swift messaging, connectivity, and operator interaction. Based on the analysis:
C (F, G, H)includes communication components, all in scope.
D (C, E, M)includes the messaging interface, GUI, and operator workstation, all in scope.Components A, B, and data exchange paths (J, K, L) are not directly in scope, though middleware (I) would be if considered separately.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Customer Security Programme – Scope and Applicability, Section: CSCF Scope Definition.
CSCF v2024, Control 1.2: Logical Access Control.
A Swift user uses an application integrating a sFTP client to push files to a service bureau sFTP server What architecture type is the Swift user? (Choose all that apply.)

A1
B
A3
A4
The Answer Is:
B, CWhat must a Swift user implement to comply with a CSCF security control?

A solution that maps the implementation guidelines described for a controls in scope components
A solution that meets the control objectives and addresses the risk drivers for the in scope components)
The Answer Is:
BExplanation:
This question addresses the implementation requirements for CSCF security controls.
Step 1: Understand CSCF Compliance
TheCSCF v2024emphasizes achieving control objectives and mitigating risk drivers for in-scope components, allowing flexibility in implementation, as perControl Objectives Overview.
Step 2: Evaluate Each Option
A. A solution that maps the implementation guidelines described for a controls in scope componentsWhile implementation guidelines exist, strict adherence is not mandatory. TheCSCF v2024allows custom solutions if they meet objectives.Conclusion: Incorrect.
B. A solution that meets the control objectives and addresses the risk drivers for the in scope componentsTheCSCF v2024andSwift CSP FAQrequire solutions to align with control objectives (e.g., security, detection) and mitigate identified risks, offering flexibility in approach.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answer isB, as theCSCF v2024prioritizes meeting objectives and addressing risks over rigid guideline mapping.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Control Objectives.
Swift CSP FAQ, Section: Implementation Flexibility.
In an entity having a small infrastructure and only 2 operators, the HR manager explains in a short interview how the security training is implemented providing one example. Would it be acceptable?

Yes. it's a risk based testing approach this can be enough in this case
No. more evidence are required
The Answer Is:
BExplanation:
This question assesses whether a short interview with the HR manager providing one example of security training implementation is acceptable for a small infrastructure with only two operators, under the Swift Customer Security Programme (CSP).
Step 1: Understand Security Training Requirements
TheSwift Customer Security Controls Framework (CSCF) v2024, underControl 5.1: Security Training and Awareness, mandates that all personnel with access to Swift-related systems (including operators) receive regular, documented security training. This includes awareness of security policies, procedures, and incident response. The control applies regardless of the size of the infrastructure.
Step 2: Analyze the Scenario
The entity has a small infrastructure with two operators, and the HR manager provides a short interview with one example of security training implementation.
TheIndependent Assessment Frameworkrequires assessors to validate the effectiveness of controls, including evidence of training completion, content, frequency, and attendance records. A risk-based approach allows flexibility, but minimum evidence standards must still be met.
Step 3: Evaluate Against CSCF Guidelines
Control 5.1specifies that training must be documented, with evidence such as training logs, attendance records, or certification. A single interview with one example does not provide sufficient evidence to demonstrate:
That all operators (both in this case) have been trained.
The frequency and comprehensiveness of the training program.
The effectiveness of the training (e.g., understanding and application).
TheSwift CSP FAQandSecurity Best Practicesnote that even for small entities, assessors must see multiple pieces of evidence (e.g., training schedules, materials, test results) to confirm compliance, especially during an independent assessment.
A risk-based testing approach (mentioned in option A) allows tailoring the depth of evidence based on risk, but it does not exempt small entities from providing more than a single anecdotal example. TheIndependent Assessment Frameworkrequires objective evidence, not just verbal assurances.
Step 4: Conclusion and Verification
The answer isB, as a short interview with one example is insufficient to meet the evidence requirements ofControl 5.1in theCSCF v2024. More evidence (e.g., training records, attendance logs, or test results) is required to validate compliance, even for a small infrastructure.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 5.1: Security Training and Awareness.
Swift Independent Assessment Framework, Section: Evidence Requirements.
Swift Security Best Practices, Section: Training Documentation.
Swift CSP FAQ, Section: Small Entity Compliance.



