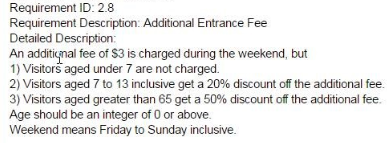
The requirement given in the image specifies an additional fee of $3 that is charged during the weekend, with some exceptions and discounts based on the age of the visitors. To test this requirement, we can use boundary value analysis, which is a specification-based test technique that involves testing the values at or near the boundaries of an equivalence partition. An equivalence partition is a set of values that are expected to be treated in the same way by the system under test. For example, based on the requirement, we can identify the following equivalence partitions for the input age:
EP1: Age < 0 (invalid)
EP2: Age = 0 (valid, no charge)
EP3: 0 < Age < 7 (valid, no charge)
EP4: Age = 7 (valid, 20% discount)
EP5: 7 < Age < 13 (valid, 20% discount)
EP6: Age = 13 (valid, 20% discount)
EP7: 13 < Age < 65 (valid, full charge)
EP8: Age = 65 (valid, 50% discount)
EP9: Age > 65 (valid, 50% discount)
The boundary values for each equivalence partition are the values at or near the edges of the partition. For example, the boundary values for EP3 are 1 and 6. The boundary values for EP4 are 6 and 7. The boundary values for EP5 are 7 and 12. And so on.
To test this requirement using boundary value analysis, we need to select one value from each boundary and test it with different combinations of weekend and weekday. For example, we can select the following values:
BV1: Age = -1 (from EP1)
BV2: Age = 0 (from EP2 and EP3)
BV3: Age = 6 (from EP3 and EP4)
BV4: Age = 7 (from EP4 and EP5)
BV5: Age = 12 (from EP5 and EP6)
BV6: Age = 13 (from EP6 and EP7)
BV7: Age = 64 (from EP7 and EP8)
BV8: Age = 65 (from EP8 and EP9)
BV9: Age = 66 (from EP9)
We can then create test cases using these values and different combinations of weekend and weekday. For example:
TC1: Age = -1, Weekend = Yes -> Invalid input
TC2: Age = -1, Weekend = No -> Invalid input
TC3: Age = 0, Weekend = Yes -> No charge
TC4: Age = 0, Weekend = No -> No charge
TC5: Age = 6, Weekend = Yes -> No charge
TC6: Age = 6, Weekend = No -> No charge
TC7: Age = 7, Weekend = Yes -> $2.40 ($3 - 20% discount)
TC8: Age = 7, Weekend = No -> No charge
TC9: Age = 12, Weekend = Yes -> $2.40 ($3 - 20% discount)
TC10: Age = 12, Weekend = No -> No charge
TC11: Age = 13, Weekend = Yes -> $2.40 ($3 - 20% discount)
TC12: Age = 13, Weekend = No -> No charge
TC13: Age = 64, Weekend = Yes -> $3
TC14: Age = 64, Weekend = No -> No charge
TC15: Age = 65, Weekend = Yes -> $1.50 ($3 - 50% discount)
TC16: Age = 65, Weekend = No -> No charge
TC17: Age = 66, Weekend = Yes -> $1.50 ($3 - 50% discount)
TC18: Age =
66, Weekend = No -> No charge
Therefore, we need a minimum of 18 valid test cases to achieve 100% boundary value coverage based on input age.
$3.01 is not a valid output boundary value because it is not a possible output value based on the requirement. The output values can only be $0, $1.50, $2.40, or $3 depending on the input age and weekend status.
You can find more information about boundary value analysis in [A Study Guide to the ISTQB® Foundation Level 2018 Syllabus], Chapter 4, Section 4.2.