CompTIA CV0-003 - CompTIA Cloud+ Certification Exam
A cloud administrator is supporting an application that has several reliability issues. The administrator needs visibility into the performance characteristics of the application. Which of the following will MOST likely be used in a reporting dashboard?
Which of the following should be enabled to reduce cloud compute costs when planning hardware capacity?
A company is comparing an application environment to be hosted on site versus a SaaS model of the same application. Which of the following SaaS-based licensing models should the administrator consider?
A cloud administrator is looking at the company's cloud services bill for the previous month. The administrator notices on the billing dashboard that certain resources are not being billed to any particular department. Which of the following actions will help correct this billing issue?
As a result of an IT audit, a customer has decided to move some applications from an old legacy system to a private cloud. The current server location is remote with low bandwidth. Which of the following is the best migration strategy to use for this deployment?
The Chief Information Officer of a financial services company wants to ensure stringent security measures are maintained while migrating customer financial information from a private cloud to the public cloud. The cloud engineer must deploy automated validation and verification checks to prevent unauthorized disclosure of financial information. Which of the following should be configured during the migration?
A cloud administrator deployed new hosts in a private cloud. After a few months elapsed, some of the hypervisor features did not seem to be working. Which of the following was MOST likely causing the issue?
A systems administrator is trying to connect to a remote KVM host. The command line appears as follows:
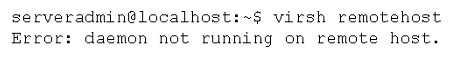
After logging in to the remote server, the administrator verifies the daemon is running. Which of the following should the administrator try NEXT?
A systems administrator deployed a new web application in a public cloud and would like to test it, but the company's network firewall is only allowing outside connections to the cloud provider network using TCP port 22. While waiting for the network administrator to open the required ports, which of the following actions should the systems administrator take to test the new application? (Select two).
An organization is conducting a performance test of a public application. The following actions have already been completed:
• The baseline performance has been established.
• A load test has passed.
• A benchmark report has been generated.
Which of the following needs to be done to conclude the performance test?



