CompTIA CV0-004 - CompTIA Cloud+ (2025)
A system surpasses 75% to 80% of resource consumption. Which of the following scaling approaches is the most appropriate?
A cloud engineer is concerned about command-and-control (C2) communication out of a cloud network over HTTPS. Which of the following should the cloud engineer implement to most efficiently identify the type of communication?
A project team is deciding how to break up a large project into smaller components so the project can be delivered without increasing the duration of the iteration cycles. Which of the following describes the grouping of the smaller components?
A log-parsing application requires significant processing power to ingest the logs streaming from web servers. The engineering team presents the cloud architect with four proposals
using the same underlying hardware. Which of the following should the cloud architect select in order to minimize the impact of an instance failure while keeping the cost as low as
possible?
Which of the following is used to detect signals and measure physical properties, such as the temperature of the human body?
Which of the following container storage types loses data after a restart?
Which of the following provides secure, private communication between cloud environments without provisioning additional hardware or appliances?
Which of the following service options would provide the best availability for critical applications in the event of a disaster?
A company migrated its CRM system to a SaaS solution. The security team is updating the RAG matrix for the newly migrated CRM. Given the following table:
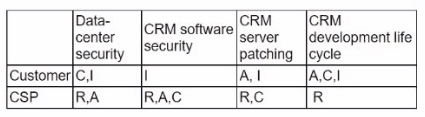
Which of the following responsibility assignments best aligns with the shared responsibility model for the new CRM?
A technician receives an email from a vendor who is requesting payment of an invoice for human resources services. The email contains a request for bank account numbers. Which of the following types of attacks does this behavior most likely indicate?



