SAP C_SEC_2405 - SAP Certified Associate - Security Administrator
Which application in SAP S/4HANA Cloud Public Edition allows you to upload employee information independent of the customers’ HR system?
What must you do if you want to enforce an additional authorization check when a user starts an SAP transaction?
Which optional components can be included when transporting a role definition from the development system to the quality assurance system? Note: There are 3 correct answers to this question.
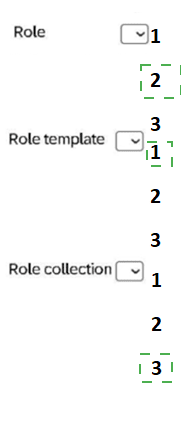
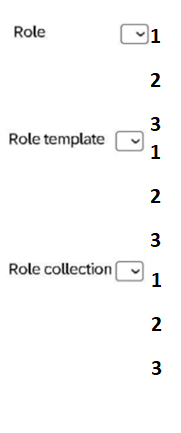
In which order do you define the security-relevant objects in SAP BTP?
Which user type in SAP S/4HANA Cloud Public Edition is used for API access, system integration, and scenarios where automated data exchange is required?
Which code does the authority-check return when a user does NOT have any authorizations for the authorization object checked?
In the SAP BTP Cockpit, at which level is Trust Configuration available? Note: There are 2 correct answers to this question.
Which cryptographic libraries are provided by SAP? Note: There are 2 correct answers to this question.
When creating PFCG roles for SAP Fiori access, what is included automatically when adding a catalog to the menu of a back-end PFCG role? Note: There are 2 correct answers to this question.
Which levels of security protection are provided by Secure Network Communication (SNC)? Note: There are 3 correct answers to this question.