CompTIA DS0-001 - CompTIA DataSys+ Certification Exam
Which of the following is a reason to create a stored procedure?
Which of the following is a characteristic of all non-relational databases?
A database administrator is concerned about transactions in case the system fails. Which of the following properties addresses this concern?
A business analyst is using a client table and an invoice table to create a database view that shows clients who have not made purchases yet. Which of the following joins ismostappropriate for the analyst to use to create this database view?
Which of the following have data manipulation and procedural scripting power? (Choose two.)
An on-premises application server connects to a database in the cloud. Which of the following must be considered to ensure data integrity during transmission?
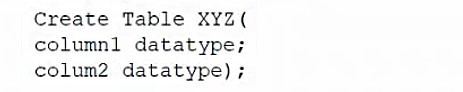
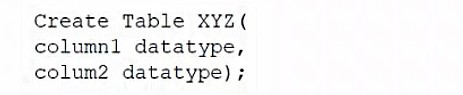
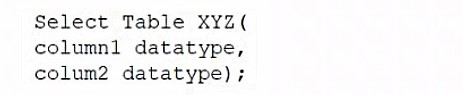
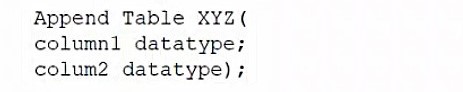
A database administrator would like to create a table named XYZ. Which of the following queries should the database administrator use to create the table?
A)
B)
C)
D)
Which of the following commands is part of DDL?
Which of the following is a result of an on-path attack on a system?
A database's daily backup failed. Previous backups were completed successfully. Which of the following should the database administrator examinefirstto troubleshoot the issue?



