ECCouncil ECSAv10 - EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram.
Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a TYPE field.
If the destination is not reachable, which one of the following are generated?
The first phase of the penetration testing plan is to develop the scope of the project in consultation with the client. Pen testing test components depend on the client’s operating environment, threat perception, security and compliance requirements, ROE, and budget.
Various components need to be considered for testing while developing the scope of the project.
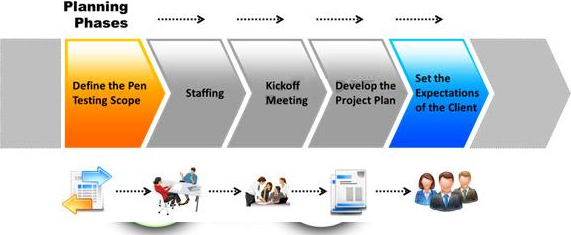
Which of the following is NOT a pen testing component to be tested?
Rule of Engagement (ROE) is the formal permission to conduct a pen-test. It provides top-level guidance for conducting the penetration testing. Various factors are considered while preparing the scope of ROE which clearly explain the limits associated with the security test.
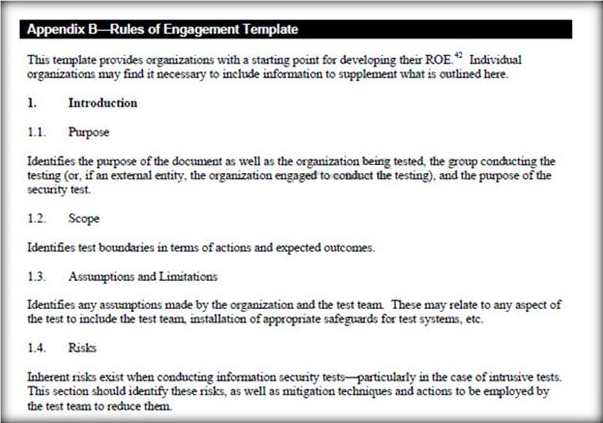
Which of the following factors is NOT considered while preparing the scope of the Rules of Engagment (ROE)?
The Internet is a giant database where people store some of their most private information on the cloud, trusting that the service provider can keep it all safe. Trojans, Viruses, DoS attacks, website defacement, lost computers, accidental publishing, and more have all been sources of major leaks over the last 15 years.
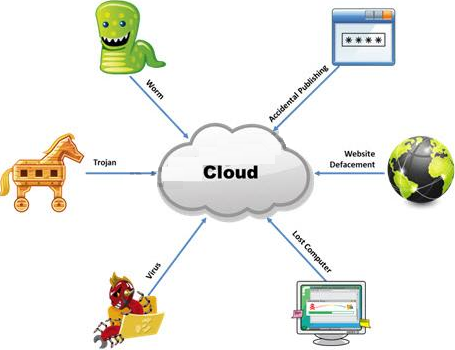
What is the biggest source of data leaks in organizations today?
Rules of Engagement (ROE) document provides certain rights and restriction to the test team for performing the test and helps testers to overcome legal, federal, and policy-related restrictions to use different penetration testing tools and techniques.

What is the last step in preparing a Rules of Engagement (ROE) document?
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.
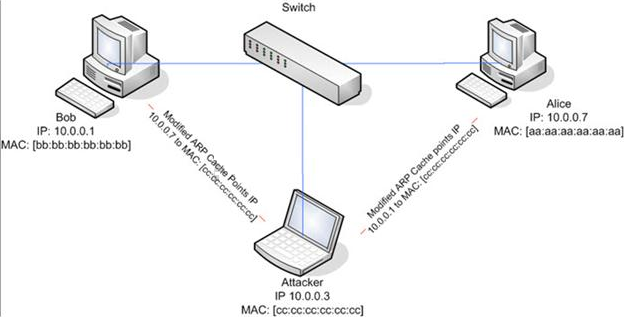
What type of attack would you launch after successfully deploying ARP spoofing?
What are the 6 core concepts in IT security?
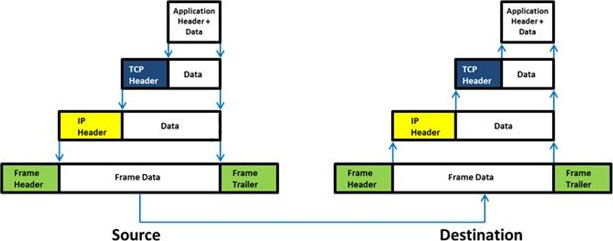
Which of the following statement holds true for TCP Operation?
What will the following URL produce in an unpatched IIS Web Server?