Fortinet FCP_FWB_AD-7.4 - FCP - FortiWeb 7.4 Administrator
Review the following configuration:

Which result would you expect from this configuration setting?
Which would be a reason to implement HTTP rewriting?
Which high availability (HA) mode uses gratuitous Address Resolution Protocol (ARP) to advertise a failover event to neighboring network devices?
What is the difference between an API gateway protection schema and a machine learning (ML) API protection schema?
You are using HTTP content routing on FortiWeb. You want requests for web application A to be forwarded to a cluster of web servers, which all host the same web application. You want requests for web application B to be forwarded to a different, single web server.
Which statement regarding this solution is true?
Refer to the exhibit.
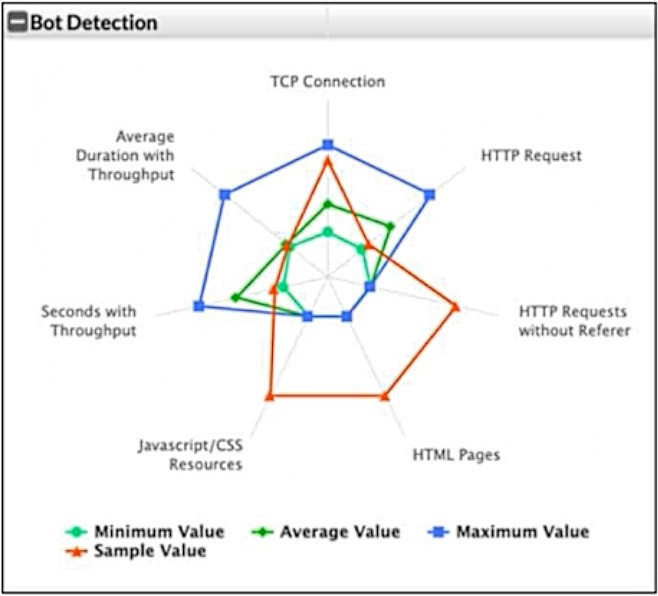
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?
A customer wants to be able to index your websites for search and advertisement purposes.
What is the easiest way to allow this on a FortiWeb?
Refer to the exhibit.
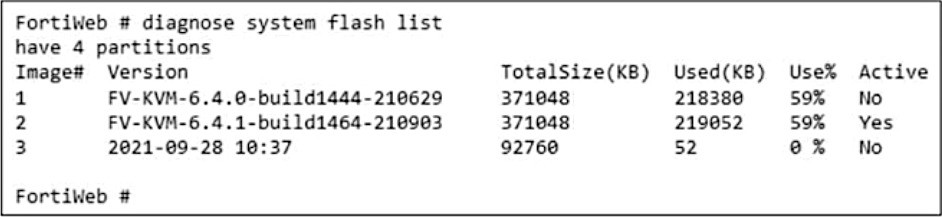
What is true about this FortiWeb device? (Choose two.)
Review the following configuration:

What are two routing behaviors that you can expect on FortiWeb after this configuration change? (Choose two.)
An administrator notices multiple IP addresses attempting to log in to an application frequently, within a short time period. They suspect attackers are attempting to guess user passwords for a secure application.
What is the best way to limit this type of attack on FortiWeb, while still allowing legitimate traffic through?



