Fortinet FCSS_SOC_AN-7.4 - FCSS - Security Operations 7.4 Analyst
Which statement describes automation stitch integration between FortiGate and FortiAnalyzer?
According to the National Institute of Standards and Technology (NIST) cybersecurity framework, incident handling activities can be divided into phases.
In which incident handling phase do you quarantine a compromised host in order to prevent an adversary from using it as a stepping stone to the next phase of an attack?
Which two ways can you create an incident on FortiAnalyzer? (Choose two.)
Refer to the exhibits.
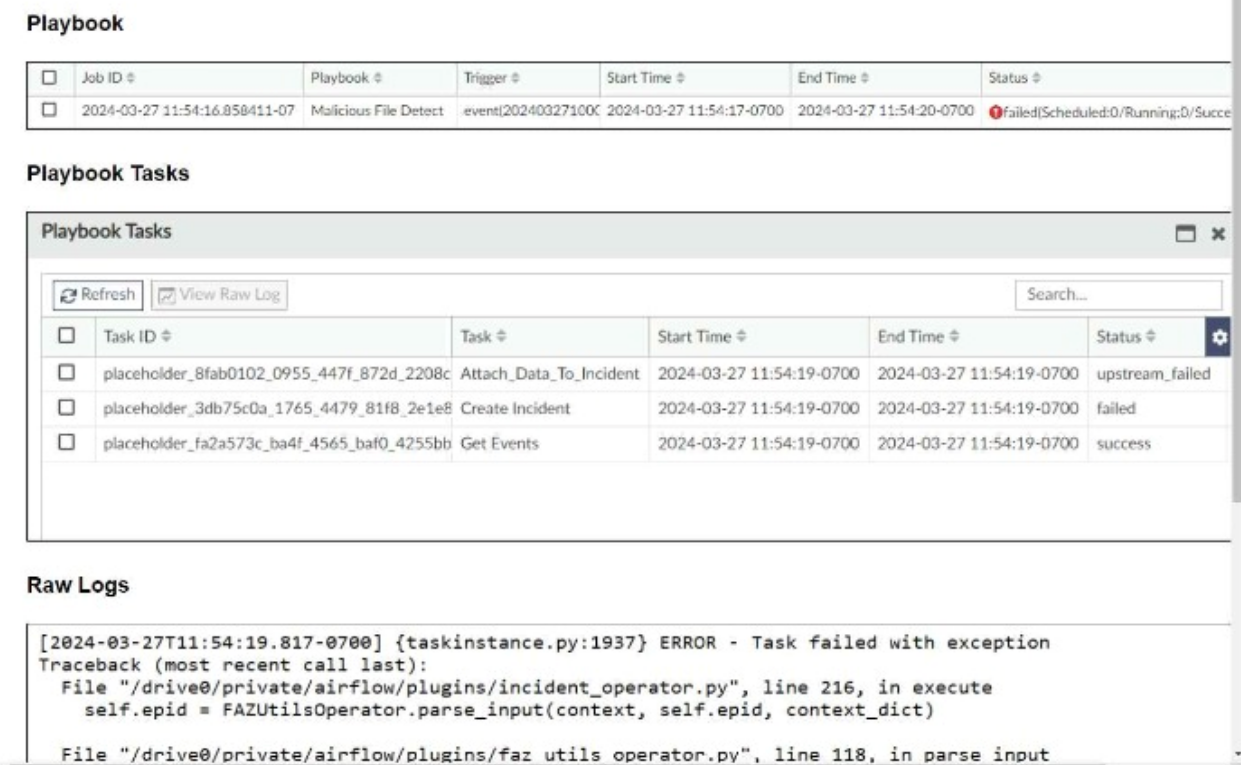
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Which two types of variables can you use in playbook tasks? (Choose two.)
Exhibit:
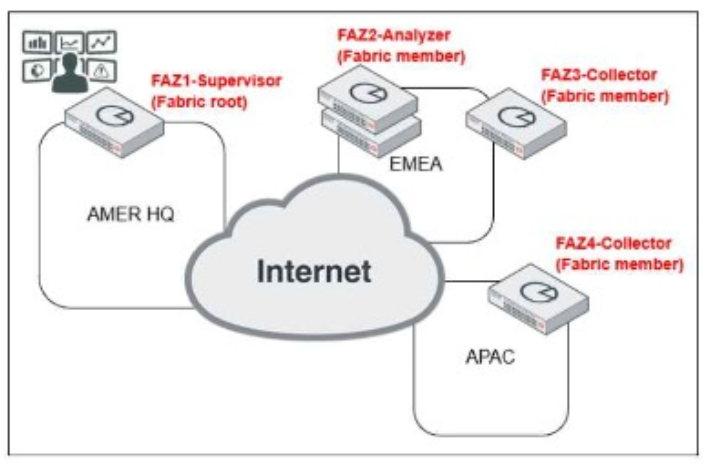
Which observation about this FortiAnalyzer Fabric deployment architecture is true?
Refer to Exhibit:
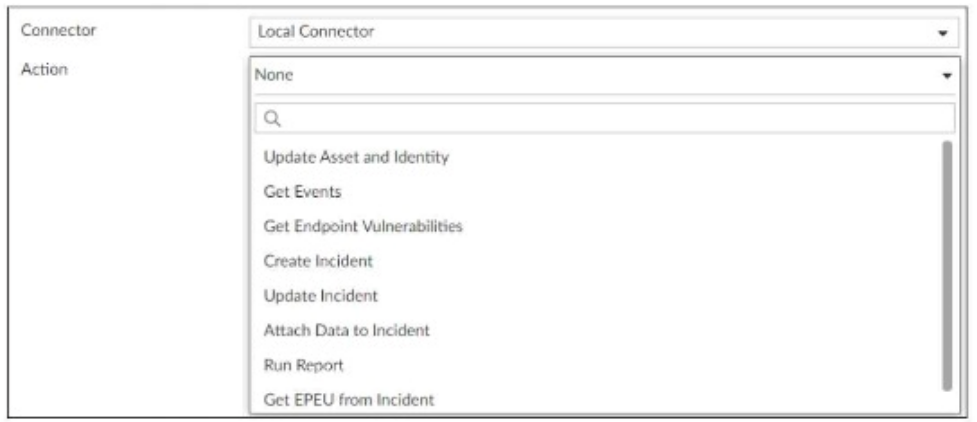
A SOC analyst is designing a playbook to filter for a high severity event and attach the event information to an incident.
Which local connector action must the analyst use in this scenario?
Refer to the exhibits.
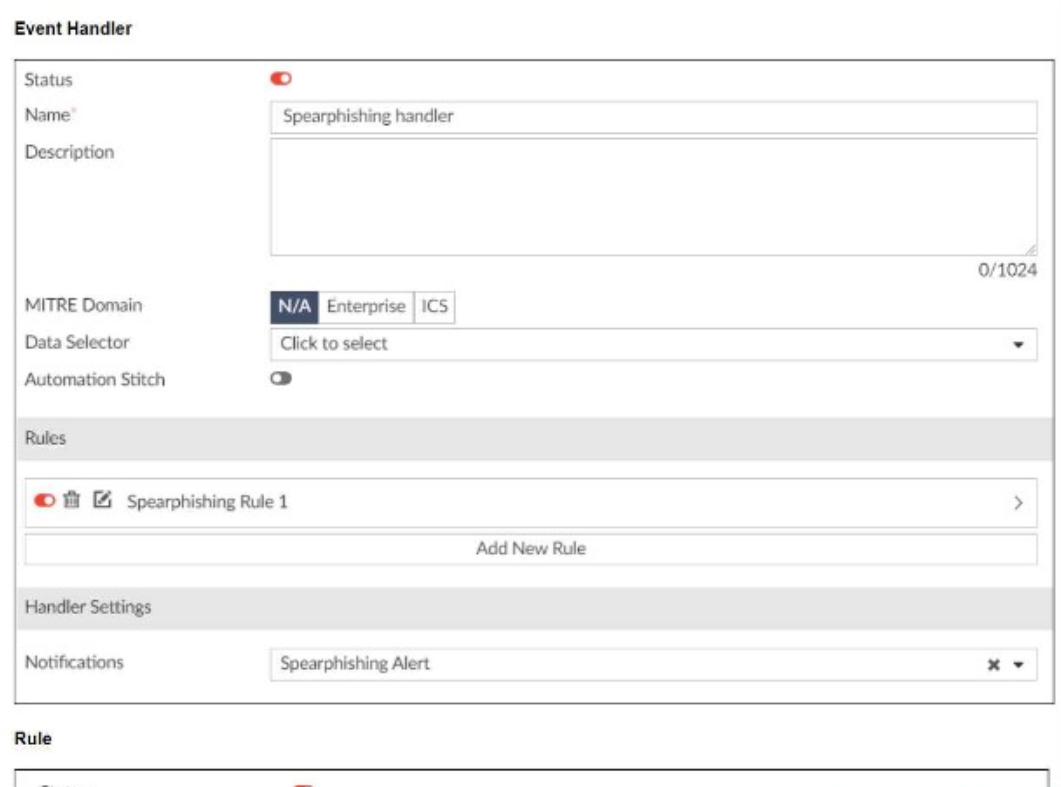
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an event?
Refer to Exhibit:
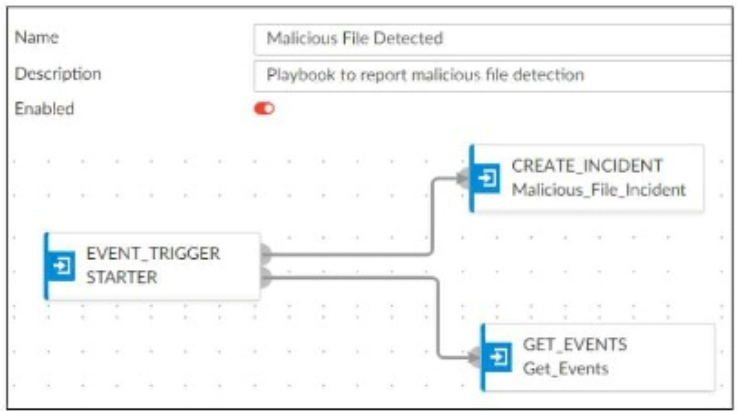
A SOC analyst is creating the Malicious File Detected playbook to run when FortiAnalyzer generates a malicious file event. The playbook must also update the incident with the malicious file event data.
What must the next task in this playbook be?



