GIAC G2700 - GIAC Certified ISO-2700 Specialist Practice Test
You work as a Security Administrator for uCertify Inc. You are working on the disaster recovery plan (DRP) for IT related infrastructure recovery / continuity. Which of the following should you include in your plan?
Each correct answer represents a complete solution. Choose all that apply.
John works as a Security Administrator for uCertify Inc. As per his past experience, he wants to make a policy stating that any hardware devices containing information about the organization should be destroyed properly before they are thrown. After applying this policy, John will be able to ensure that the information on the devices will not fall into the hands of unauthorized persons after properly discarding the devices. Which of the following types of policies is John going to create?
You work as a Database Administrator for Bluewell Inc. The company has a SQL Server 2005 computer. The company asks you to implement a RAID system to provide fault tolerance to a database. You want to implement disk mirroring. Which of the following RAID levels will you use to accomplish the task?
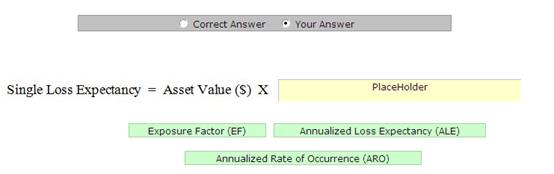
Drop the appropriate value to complete the formula.
Which of the following activities are performed by the 'Do' cycle component of PDCA (plan-docheck- act)?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements is true about residual risks?
Which of the following statements is true about exposure factor?
In which of the following social engineering attacks does an attacker first damage any part of the target's equipment and then advertise himself as an authorized person who can help fix the problem.
You work as a Security Administrator for uCertify Inc. You have been assigned the task to apply a data availability solution based on a striped disk array without redundancy. Which of the following will you use to accomplish the task?
Which of the following tools can be used to detect steganography?



