GIAC GCFA - GIACCertified Forensics Analyst
Adam, a malicious hacker has successfully gained unauthorized access to the Linux system of
Umbrella Inc. Web server of the company runs on Apache. He has downloaded sensitive documents and database files from the computer. After performing these malicious tasks, Adam finally runs the following command on the Linux command box before disconnecting. for (( i = 0;i<11;i++ )); do
dd if=/dev/random of=/dev/hda && dd if=/dev/zero of=/dev/hda done
Which of the following actions does Adam want to perform by the above command?
You want to upgrade a partition in your computer's hard disk drive from FAT to NTFS. Which of the following DOS commands will you use to accomplish this?
Adam works as a Security Administrator for Umbrella Inc. He is responsible for securing all 15 servers of the company. To successfully accomplish the task, he enables the hardware and software firewalls and disables all unnecessary services on all the servers. Sales manager of the company asks Adam to run emulation software on one of the servers that requires the telnet service to function properly. Adam is concerned about the security of the server, as telnet can be a very large security risk in an organization. Adam decides to perform some footprinting, scanning, and penetration testing on the server to checkon the server to check the security. Adam telnets into the server and writes the following command:
HEAD / HTTP/1.0
After pressing enter twice, Adam gets the following results:
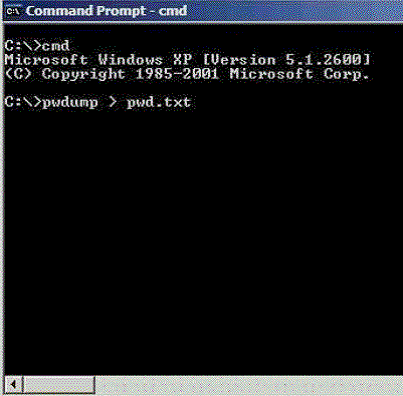
Which of the following tasks has Adam just accomplished?
Which of the following directories in Linux operating system contains device files, which refers to physical devices?
Which of the following tools can be used to perform a whois query?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate the BlackBerry, which is suspected to be used to hide some important information. Which of the following is the first step taken to preserve the information in forensic investigation of the BlackBerry?
Which of the following is the process of comparing cryptographic hash functions of system executables and configuration files?
Which of the following is the process of overwriting all addressable locations on a disk?
An organization wants to mitigate the risks associated with the lost or stolen laptops and the associated disclosure laws, while reporting data breaches. Which of the following solutions will be best for the organization?
Which of the following files in LILO booting process of Linux operating system stores the location of Kernel on the hard drive?



