GIAC GSEC - GIAC Security Essentials
In PKI, when someone wants to verify that the certificate is valid, what do they use to decrypt the signature?
What is the name of the command-line tool for Windows that can be used to manage audit policies on remote systems?
You are reviewing a packet capture file from your network intrusion detection system. In the packet stream, you come across a long series of "no operation" (NOP) commands. In addition to the NOP commands, there appears to be a malicious payload. Of the following, which is the most appropriate preventative measure for this type of attack?
Which of the following features of Windows 7 allows an administrator to both passively review installed software and configure policies to prevent out-of-date or insecure software from running?
Which aspect of UNIX systems was process accounting originally developed for?
Analyze the following screenshot. What conclusion can be drawn about the user account shown?

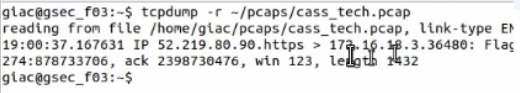
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap.
What is the source port number?
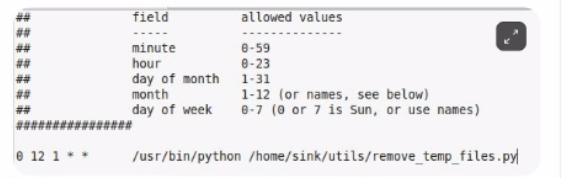
Analyze the file below. When will the program /home/sink/utils/remove temp hies.py run?
On which of the following OSI model layers does IPSec operate?
Which of the following tools is used to configure, control, and query the TCP/IP network interface parameters?



