GIAC GSEC - GIAC Security Essentials
Who is responsible for deciding the appropriate classification level for data within an organization?
In the AGULP model, who should be assigned permissions and privileges?
Which of the following works at the network layer and hides the local area network IP address and topology?
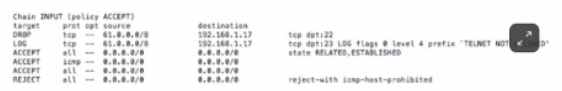
Based on the iptables output below, which type of endpoint security protection has host 192.168.1.17 implemented for incoming traffic on TCP port 22 (SSH) and TCP port 23 (telnet)?
What is the fundamental problem with managing computers in stand-alone Windows workgroups?
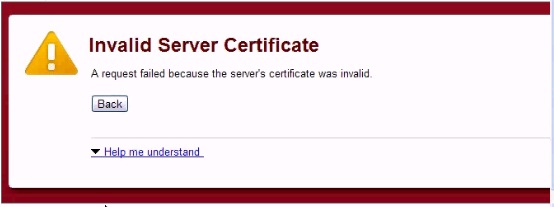
An employee attempting to use your wireless portal reports receiving the error shown below. Which scenario is occurring?
Which of the following statements about Microsoft's VPN client software is FALSE?
The TTL can be found in which protocol header?
Where are user accounts and passwords stored in a decentralized privilege management environment?
Which of the following fields CANNOT be hashed by Authentication Header (AH) in transport mode?



