GIAC GSEC - GIAC Security Essentials
Analyze the screenshot below. In what order should the vulnerabilities be remediated?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to change the startup shell of Maria from bash to tcsh. Which of the following commands will John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Net Perfect Inc. The company has a Linux-based network. You are configuring an application server. An application named Report, which is owned by the root user, is placed on the server. This application requires superuser permission to write to other files. All sales managers of the company will be using the application. Which of the following steps will you take in order to enable the sales managers to run and use the Report application?
What would the following IP tables command do?
IP tables -I INPUT -s 99.23.45.1/32 -j DROP
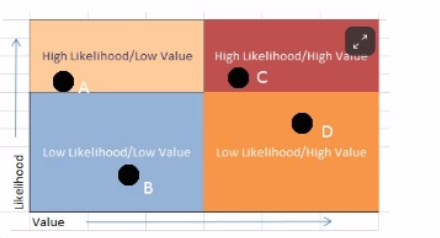
Which of the following elements is the most important requirement to ensuring the success of a business continuity plan?
Which port category does the port 110 fall into?
What could be used to mitigate hash collisions?
When using Pretty Good Privacy (PGP) to digitally sign a message, the signature is created in a two-step process. First, the message to be signed is submitted to PGP's cryptographic hash algorithm. What is one of the hash algorithms used by PGP for this process?
During which of the following steps is the public/private key-pair generated for Public Key Infrastructure (PKI)?
When no anomaly is present in an Intrusion Detection, but an alarm is generated, the response is known as.



