GIAC GSLC - GIAC Security Leadership Certification (GSLC)
In which of the following social engineering attacks does an attacker first damage any part of the target's equipment and then advertise himself as an authorized person who can help fix the problem.
Which of the following statements are true about an application-level gateway?
Each correct answer represents a complete solution. Choose all that apply.
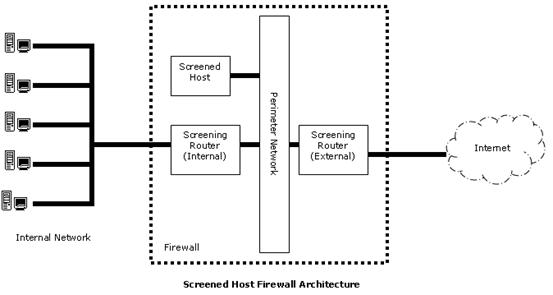
In the image of the Screened Host Firewall Architecture given below, select the element that is commonly known as the access router.
Which of the following is an entry in an object's discretionary access control list (DACL) that grants permissions to a user or group?
Which of the following statements about reconnaissance is true?
Which of the following types of cryptography algorithms uses the MD series of encryption algorithms?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.weare-secure.com. He enters a single quote in the input field of the login page of the We-are- secure Web site and receives the following error message:
Microsoft OLE DB Provider for ODBC Drivers error '0x80040E14'
This error message shows that the We-are-secure Website is vulnerable to __________.
You are concerned about possible hackers doing penetration testing on your network as a prelude to an attack. What would be most helpful to you in finding out if this is occurring?
Andrew works as a Software Developer for Mansoft Inc. The company's network has a Web server that hosts the company's Web site. Andrew wants to enhance the security of the Web site by implementing Secure Sockets Layer (SSL). Which of the following types of encryption does SSL use?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for PassGuide Inc. Adam, your assistant, wants to perform a backup of the server. Which of the following authentication methods will you assign to Adam?
Mark works as a Network Administrator for We-are-secure Inc. He finds that the We-are-secure server has been infected with a virus. He presents to the company a report that describes the symptoms of the virus. A summary of the report is given below:
This virus has a dual payload, as the first payload of the virus changes the first megabyte of the hard drive to zero. Due to this, the contents of the partition tables are deleted and the computer hangs.
The second payload replaces the code of the flash BIOS with garbage values. This virus spreads under the Portable Executable File Format under Windows 95, Windows 98, and Windows ME.
Which of the following viruses has the symptoms as the one described above?
You are the project manager for the GHY Organization. A stakeholder has presented a change to your project that will cause the project scope to increase considerably. You are considering the change for approval and you need to review the impact of the change on all areas of the project. What change control system component is responsible for guiding the review of the impact of all changes on the project management knowledge areas?
Which of the following protocols provides mail forwarding and information storing features?
Fill in the blank with the appropriate type of router.
A ______ router performs packet-filtering and is used as a firewall.
Janet is the project manager of the NHQ Project for her company. Janet is nearly done leading the project and there have been no cost or schedule overruns in the development of the new software for her company. The project team has been completing their work on time and there is still $75,000 left in the project budget. Janet decides to have the project team implement some extra features to the project scope to use all of the $75,000 in the budget even though the customer didn't specifically ask for the added features. This scenario is an example of which one of the following?



