GIAC GSNA - GIAC Systems and Network Auditor
Which of the following techniques can be used to determine the network ranges of any network?
You work as a Network Administrator for Tech-E-book Inc. You are configuring the ISA Server 2006 firewall to provide your company with a secure wireless intranet. You want to accept inbound mail delivery though an SMTP server. What basic rules of ISA Server do you need to configure to accomplish the task.
You are the Security Administrator for an Internet Service Provider. From time to time your company gets subpoenas from attorneys and law enforcement for records of customers' access to the internet. What policies must you have in place to be prepared for such requests?
You work as a Network Administrator for Tech Perfect Inc. You have a laptop running Windows Vista Ultimate. You want to configure Windows Defender on your laptop so that it does not take any action automatically whenever it scans malicious software. Rather, it should recommend the action and wait for your approval for taking any action. Which of the following actions will you take to accomplish the task?
Which of the following services are provided by the proxy servers?
Mike works as a Network Engineer for XYZ CORP. The company has a multi-platform network. Recently, the company faced lots of blended threat issues that lead to several drastic attacks. Mike has been assigned a project to manage the resources and services of the company through both Intranet and Internet to protect the company from these attacks. Mike needs a system that provides auto-discovering and network topology building features to allow him to keep an intuitive view of the IT infrastructure. What will Mike use to meet the requirement of the project?
Which of the following types of authentication tokens forms a logical connection to the client computer but does not require a physical connection?
In which of the following techniques does an attacker take network traffic coming towards a host at one port and forward it from that host to another host?
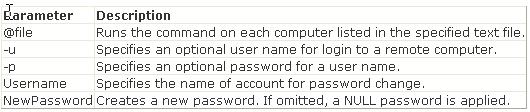
Which of the following commands can be used to format text files?
You work as an IT Technician for XYZ CORP. You have to take security measures for the wireless network of the company. You want to prevent other computers from accessing the company's wireless network. On the basis of the hardware address, which of the following will you use as the best possible method to accomplish the task?



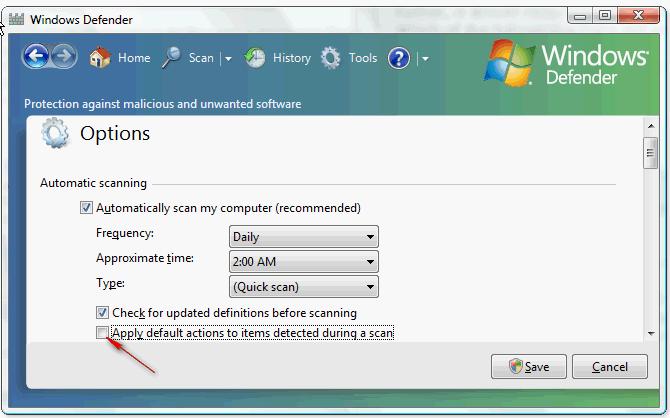 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG