GIAC GSNA - GIAC Systems and Network Auditor
Network mapping provides a security testing team with a blueprint of the organization. Which of the following steps is NOT a part of manual network mapping?
Which of the following statements about URL rewriting are true?
You work as the Network Administrator for a company. You configure a Windows 2000-based computer as the Routing and Remote Access server, so that users can access the company's network, remotely. You want to log a record of all the users who access the network by using Routing and Remote Access. What will you do to log all the logon activities?
You have purchased a laptop that runs Windows Vista Home Premium. You want to protect your computer from malicious applications, such as spyware, while connecting to the Internet. You configure Windows Defender on your laptop to schedule scan daily at 2 AM as shown in the image below:
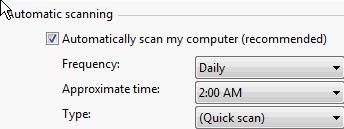
You want Windows Defender to scan the laptop for all the known spyware and other potentially unwanted software, including the latest one. You do not want to manually perform this task. Which of the following actions will you perform to accomplish the task?
Which of the following processes is described in the statement below? "This is the process of numerically analyzing the effect of identified risks on overall project objectives."
You work as the Network Administrator for XYZ CORP. The company has a Linux-based network. You are a root user on the Red Hat operating system. You want to see first five lines of the file /etc/passwd. Which of the following commands should you use to accomplish the task?
Which of the following are known as safety critical software?
Which of the following statements are true about MS-CHAPv2?
Which of the following processes are involved under the COBIT framework?
You work as a Software Developer for XYZ CORP. You create a SQL server database named DATA1 that will manage the payroll system of the company. DATA1 contains two tables named EmployeeData, Department. While EmployeeData records detailed information of the employees, Department stores information about the available departments in the company. EmployeeData consists of columns that include EmpID, EmpName, DtOBrth, DtOJoin, DeptNo, Desig, BasicSal, etc. You want to ensure that each employee ID is unique and is not shared between two or more employees. You also want to ensure that the employees enter only valid department numbers in the DeptNo column. Which of the following actions will you perform to accomplish the task?



