GIAC GSSP-NET-CSHARP - GIAC GIAC Secure Software Programmer - C#.NET
Smith works as a Software Developer for ABC Inc. He creates an application using Visual
Studio .NET 2005. The application displays "Welcome to ABC" on the top-left corner of a form. He writes the following code:
StringBuilder strbuild1 = new StringBuilder(20);
strbuild1.Append("'Welcome");
strbuild1.Append(" ");
strbuild1.Append("to");
strbuild1.Append(" ");
strbuild1.Append("ABC'");
string str1 = strbuild1.ToString();
Console.WriteLine(str1);
Console.ReadLine();
What is the main purpose of using StringBuilder object in the application?
You work as a Software Developer for ABC Inc. You use C# .NET to develop a windows application. The application will implement a role-based authorization scheme that is based on a Microsoft SQL Server database of user names. Users will enter their names in a text box named UserName. You must ensure that users are assigned the supervisor role and the PG role by default. Which of the following code segments will you use to accomplish this task?
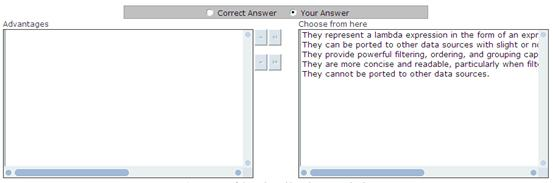
You work as a Web Application Developer for SunInfo Inc. The company uses Visual Studio 2008 as its application development platform. You create a Web application using .NET Framework 3.5. You use foreach loops to retrieve data from a collection. Now, you want to use LINQ queries instead of foreach loops. Choose the advantages of using LINQ queries over foreach loops.
You work as a Software Developer for ABC Inc. You develop a Web application that contains several Web pages. The Web pages contain several Web server controls that implement validation controls for user input validation. Under which of the following circumstances will you perform user input validation programmatically for Web server controls?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for Mansoft Inc. You create an ASP.NET Web application named MyWebApp. You implement a security protocol to transmit secured data between a client and a server. You try to authenticate the client computer. However, you are unable to do so, and the AuthenticationException exception is thrown. Which of the following classes will you use to accomplish this task?
Each correct answer represents a complete solution. Choose two.
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a Windows Forms application by using the .NET Framework. The application executes a background thread. You are required to create the thread to exit, but you must also inform the main thread when the background thread has finished. What will you do to accomplish this?
You work as a Software Developer for ABC Inc. The company uses Visual Studio.NET 2005 as its application development platform. You are creating an application using .NET Framework 2.0. You are using string datatype in the application to store text based information. You want to match character in a string in such a way that the match must occur at the point where the previous match ended. Which of the following characters will you use to accomplish the task?
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its application development platform. Allen creates an application that will be used to handle security information related to the company. He wants to secure the application by using the most secure authentication method. The method should have a strong key for encryption and send the encrypted password across the network. Which of the following authentication methods will Allen use to accomplish the task?
You work as an Enterprise Application Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its application development platform. You create a logging utility class using .NET Framework 3.5. The utility class writes logs to event log services. You are required to ensure that the client applications that use the utility class can create an instance of the utility class only if they have access rights to write to the event log services.
What will you do?
Richard works as a Software Developer for BlueWell Inc. He is writing a component that will be shared by multiple applications. He wants to install the component in the GAC (Global Assembly Access) To install a component in the GAC, he requires to provide a strong name to the component. Which of the following tools will he use to accomplish this task?



