Huawei H12-722 - Huawei Certified ICT Professional - Constructing Service Security Network (HCIP-Security-CSSN V3.0)
Since the sandbox can provide a virtual execution environment to detect files in the network, the sandbox can be substituted when deploying security equipment
Anti-Virus, IPS, spam detection and other equipment.
Buffer overflows, Trojan horses, and backdoor attacks are all attacks at the application layer.
Regarding the network intrusion detection system (NIDS), which of the following statements is wrong?
Misuse detection is through the detection of similar intrusions in user behavior, or those that use system flaws to indirectly violate system security rules
To detect intrusions in the system. Which of the following is not a feature of misuse detection 2
The anti-tampering technology of Huawei WAF products is based on the cache module. Suppose that when user A visits website B, website B has page tampering.
Signs: The workflow for the WAF tamper-proof module has the following steps:.
â‘ WAF uses the pages in the cache to return to the client;
â‘¡WAF compares the watermark of the server page content with the page content in the cache
â‘¢Store the content of the page in the cache after learning
â‘£ When the user accesses the Web page, the WAF obtains the page content of the server
⑤WAF starts the learning mode to learn the page content of the user's visit to the website;
For the ordering of these steps, which of the following options is correct?
The realization of content security filtering technology requires the support of the content security combination license.
When using the two-way SSL function to decrypt HTTPS packets, the value of the reverse proxy level represents the number of times the packet can be decrypted.
What content can be filtered by the content filtering technology of Huawei USG6000 products? (multiple choice)
For special message attacks, which of the following option descriptions is correct?
A Special control packet attack is a potential attack and does not have direct destructive behavior
B. The attacker probes the network structure by sending special control messages to launch a real attack.
C. Special control message attacks do not have the ability to detect the network structure. Only scanning attacks can detect the network.
D. Special control message items can only use ICMP to construct attack messages.
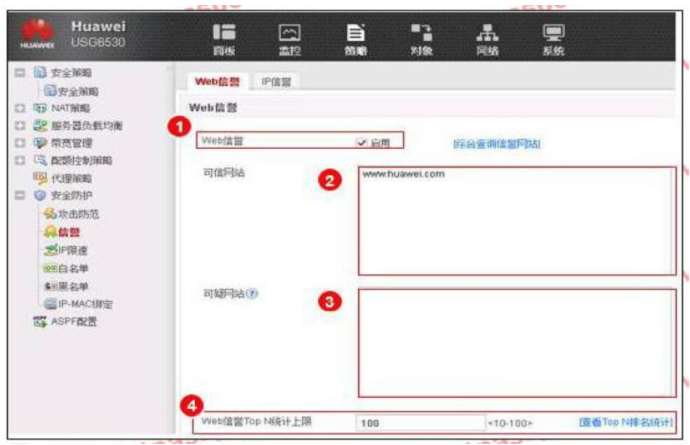
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?