Huawei H12-722_V3.0 - HCIP-Security-CSSN V3.0
Which of the following elements does PDCA include? (Choose 3 answers)
Which of the following options is wrong for the description of the cleaning center?
In Huawei USG6000 products, IAE provides an integrated solution, all content security detection functions are integrated in a well-designed
In the high-performance engine. Which of the following is not the content security detection function supported by this product?
In the Huawei USG6000 product, after creating or modifying the security configuration file, the configuration content will not take effect immediately: you need to click the "Prompt" in the upper right corner of the interface.
"Hand in" to activate.
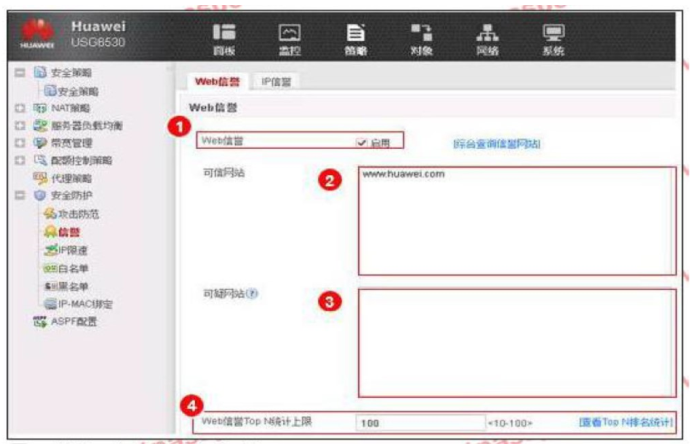
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
Regarding the statement of the mail protocol, which of the following is correct? (multiple choice)
Abnormal detection is to establish the normal behavior characteristic profile of the system subject through the analysis of the audit data of the system: check if the audit data in the system
If there is a big discrepancy with the normal behavior characteristics of the established subject, it is considered an intrusion. Nasu must be used as the system subject? (multiple choice)
If a company wants to detect image files, Shellcode code files and PDF files, which of the following types of sandboxes can be used? (More
155955cc-666171a2-20fac832-0c042c0420
select)
Which of the following descriptions about the black and white lists in spam filtering is wrong? c
Huawei WAF products are mainly composed of front-end execution, back-end central systems and databases. Among them, the database mainly stores the front-end detection rules and black
Whitelist and other configuration files.
A True
B. False



