Huawei H12-722_V3.0 - HCIP-Security-CSSN V3.0
Among the following options, which attack is a malformed packet attack based on the TCR protocol?
For the description of the Anti DDOS system, which of the following options is correct? C
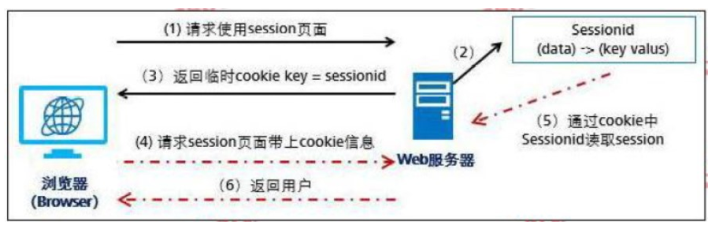
The process of a browser carrying a cookie to request resources from a server is shown in the following figure. Which of the following steps contains SessionID information in the message?
If the processing strategy for SMTP virus files is set to alert, which of the following options is correct?
The anti-virus feature configured on the Huawei USG6000 product does not take effect. Which of the following are the possible reasons? (multiple choice)
When you suspect that the company's network has been attacked by hackers, you have carried out a technical investigation. Which of the following options does not belong to the behavior that occurred in the early stage of the attack?
URL filtering technology can perform URL access control on users according to different time objects and address objects to achieve precise management of users.
The purpose of the Internet behavior.
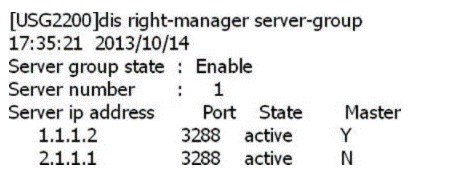
SACG query right-manager information as follows, which options are correct? (Select 2 answers)
In the construction of information security, the intrusion detection system plays the role of a monitor. It monitors the flow of key nodes in the information system.
In-depth analysis to discover security incidents that are occurring. Which of the following are its characteristics?. c0O
Buffer overflows, Trojan horses, and backdoor attacks are all attacks at the application layer.



